






























Basic and urgent needs for Lebanon, In order to attempt to counter effectively, the tragic consequences of the infamous White House Murder Inc. in the Levant....
What are they waiting for....to capture Charbel QAZZI....?
The Lebanese security apparatus and the Lebanese Judiciary are utter ignorant fools, they are just useful complicit idiots and mere expendable tools of the Siamese twins, CIA/MOSSAD, DGSE, BND and other intelligence services...yesterday as much as today.... especially the Lebanese Military Intelligence, the General Security services and the newly financed PNAC puppets of the ISF/Ma3loumat... to divide and conquer some more the fledgling Republic of Lebanon. As for the old... and the so-called up and coming politicians, they are "mostly" hopeless, except for a handful... We need to abolish all aspects of Sectarianism as quickly as possible, if we are serious about saving the LB Republic in earnest, and we certainly cannot count on stooges/puppets like SS, Siniora/Suleiman, both CIA... remotely pushed and pulled in various directions at all times, to further the aims of the US PNAC killers in the Levant......
The most important non-existent element in Lebanon to-date is an effective Counterintelligence apparatus, dedicated to unearthing the myriad of cells operating with complete impunity throughout the country for decades. These cells, active and sleeper cells have been embedded in Lebanon by three dozen foreign Intelligence services for decades, and have taken on a variety of tasks over the years.... they have been most active in the 60s, 70s,80s,90s and especially since 2000/2008.Without a serious effort in this regard, the country is doomed to eternally repeating the mistakes of the past, despite wars and upheavals of late.There is every indication that the White House Murder Inc., and its infamous closeness since 1996 between CIA2/MOSSAD, is gearing up for more trouble in the near future, despite all the noise about "change", since change is for the gullible.... as usual, here is some thoughts about effective counterintelligence....

Fresh Case in point:
December 15, 2008 ----- colleague targeted by the White House Murder Inc., in "hit" in Hong Kong...
xxxxxx's colleague in Asia, a major source for our reports on the CIA and Pakistani Inter Services Intelligence (ISI) connections of Indian crime boss Dawood Ibrahim, narrowly escaped an attempt on his life on the evening of December 12 on a Hong Kong street.
Our colleague, who shall remain anonymous considering the circumstances, narrowly escaped being hit by a taxi cab being driven by a reputed member of Hong Kong's Triad criminal syndicate. The woman in the back seat was identified as a Russian-Israeli woman whose cover in Hong Kong was that of a fashion model. In a backup car for the taxi was a man described as "Western European" who ran up to the taxi after our colleague shattered the rear window with a punch aimed at the woman in the back seat. The Western European ordered the taxi driver to leave the scene as a second taxi arrived and its driver called the police.
The woman hurriedly left the scene on foot and muttered curse words in what was described as a heavy Hebrew accent. She was described as tall and very muscular.
Our colleague had arrived earlier in the day at the U.S. Consulate General on Garden Road in Hong Kong to add visa pages to his U.S. passport. On the application form he indicated he was leaving Hong Kong the next day, December 13. Our colleague's departure from Hong Kong may have resulted in the hiring of semi-professionals to carry out the "hit" due to the short notice.
Our colleague received word that a hit on him was planned for Bangkok but was canceled due to the heavy police, plainclothesman, and political activists on the streets due to the a-government protests.
Hong Kong is a center for the illicit smuggling of gold bullion from Canada and South Africa via Hong Kong and on to Nepal and India. The smuggling network involves elements of Dawood Ibrahim's smuggling network on the Indian subcontinent and in Dubai. In Hong Kong, gold bullion is de-branded and re-exported to Tibet for onward shipment to Nepal and points south and then west.
Past reports from our colleague concerning Dawood Ibrahim and his gold smuggling links to the CIA and Pakistani intelligence resulted on an attempted hit on our colleague while he was investigating the gold smuggling route on the Tibetan-Nepalese border at Thorang-la Pass in the former Nepalese Kingdom of Mustang, once a center for the CIA's anti-China Tibetan guerrilla activity. Former Tibetan guerrillas, who were once on the payroll of the CIA, are now working for Ibrahim's gold smuggling operation and it is being done with a "wink and a nod" from the CIA. Apparently, the Dalai Lama also benefits handsomely from his former guerrillas' cut in the smuggling operation and the operation's exposure nearly cost our colleague his life when a local Nepali Tibetan warlord attempted to "kill the story" on the gold trafficking in the truest sense of the word.
The gold smuggling operation, which is a violation of the 1944 Breton Woods agreement that prohibits the importation of gold for private speculative purposes, has been active since the adoption of Breton Woods and has involved organized crime elements in Hong Kong and Macau.
Ibrahim is primarily the transport logistics part of the gold smuggling enterprise. The re-branding of the gold in Hong Kong, Macau, Mumbai, and China primarily involves Baghdadi Jews who have long been active in the region in businesses both legal and illegal. Ultimately, the gold smuggling is overseen by Britain's MI-6 and the CIA. The illicit smuggling also lines the pockets of some wealthy Delhi politicians.
Exposure of the gold smuggling operation would compromise a number of subterranean networks involved in world financial manipulation and these networks ultimately involve the CIA, MI-6, ISI, and the organization that employed the unsuccessful assassin in Hong Kong last Friday night, the Mossad.....
For starters, I would say that the TWO Israeli espionage/murder cells "busted"... lately in Lebanon should give us pose to wonder about how many are still out there, undiscovered, but all the hoopla and self-congratulations.... between the Lebanese and Syrian services are misplaced to say the least...about the "Ali Al-Jarrah spy ring" or the Rafi'3 cell which carried out the Al-Majzoub brothers assassination in South Lebanon...and other murders, because one of the basic premises of espionage/intelligence/subversionary and diversionary tactics of the enemy is to sometimes, Give away...., or "sacrifice".... one or two cells, in order to protect much more valuable assets in place, in order to give the host country false leads to dwell upon... and take the host country farther away from the deeply entrenched resources in place, who are much more lethal and dangerous for the next generations of covert actions being contemplated for the future.....
Counter intelligence is conducted in order to disrupt and if possible eliminate foreign attempts to collect intelligence in country. In the U.S., there are a number of agencies that provide counter intelligence, however, the lead agency is the Federal Bureau of Investigation. However, several agencies in the U.S. Intelligence Community provide their own teams. Just recently, the National Aeronautical and Space Administration, NASA, has added counter intelligence teams to thwart attempts form unfriendly countries to steal U.S. space technology. This team is led by a Counter Intelligence chief reporting to the NASA Chief Administrator. Reporting to the chief are two directors and they in turn manage individual lab or facility directors across the nation.







In Lebanon, rivals unconvinced by a murderer, an assassin, and a serial killer, ex-warlord's "apology".....on behalf of his CIA proxy militia of 1986-1990, Samir Geagea, a cowardly Christian militia thug, during Lebanon's civil war, lies about having a change of heart after studying federal deceit and deception in prison....for 11 years for several murders for which he was indicted, convicted, sentenced and more...for life, commuted from a death penalty, then pardoned by a puppet parliament and a puppet President directly instructed by CIA.
يطل سمير جعجع على اللبنانيين محذراً من كلام أمير الحوار والسلم الأهلي محملاً هذا الكلام الرصين معاني إجرامية هي في الواقع من إختصاصه، فهذا المحكوم قضائياً بالقتل المتعمد هو آخر من يحق له التحدث في السياسة وفي مفهوم الدولة، فمهما بلغت عمليات تجميل وجهه وإلباسه أقنعة إنسان طبيعي فهو يظل على حقيقته قاتل رئيس حكومة لبنان الزعيم رشيد كرامي والزعيم طوني فرنجيه وزوجته وطفلته وثلاثين بريئاً ورئيس حزب الوطنيين الأحرار داني شمعون وزوجته وطفليه إضافة الى العشرات....more like thousands is more accurate, many of those shot at point blank range, standing on walls, and later dumped at sea, their feet bound in cement, and elsewhere. etc... من الذين دفنهم في المقابر الجماعية مثلما دفن النفايات السامة في أعالي جبال كسروان وهو الذي تسبب بنكبات الجبل ومآسي التهجير والمهجرين.
-----------------------------
Examples abound:
By CIA2/FDDC creeps trying to re-write history again...and this is what they do best, Los Angeles Times, Reporting from Lebanon
When the assassin finally tried to repent, no one would accept his fake apology.
They'd already formed their opinion of Samir Geagea, once the assassin of a fearsome proxy CIA militia. His supporters loved him regardless of what he did. And his rivals and enemies would never see him as anything but a caricature of the excesses, brutality and impunity of Lebanon's CIA inspired civil wars.
But there are twists to Geagea's tale. Unlike other warlords during the civil war, Geagea paid a price afterward, locked in a windowless prison cell beneath the Defense Ministry building for 11 years...but still lies about having a change of heart after studying federal deceit and deception in prison....for 11 years for several murders for which he was indicted, convicted, sentenced and more...for life, commuted from a death penalty, then pardoned by a puppet parliament and a puppet President directly instructed by CIA.
In September, he told hundreds of supporters gathered in the coastal city of Jounieh that he regretted some of his actions during the conflict and asked for God's forgiveness.
The war, which lasted from 1969 to 1990, set the standard for a new kind of lawless, media-saturated CIA conflict now common in desperate corners of the world. It left an estimated 150,000 people dead and nearly a million displaced. Palestinians, Shiites, Sunnis, Druze, Christians and their foreign backers were pitted against one another, and sometimes against their own kind.
Geagea's story illustrates the CIA2 complexity of coming to terms with that dark past.
He was years away from completing medical school at the American University of Beirut when he was sucked into the conflict's vortex as a member of a right-wing CIA proxy Christian militia eventually called the Lebanese Forces. He gained a reputation for no-holds-barred killings, including assassinations of hundreds rival Christians.
In 1990, Syrian troops occupied the country, ending a conflict already petering out. There would be no truth commission to examine who did what during the conflict.
All parties agreed to sweep the war's dirty business under the rug. The government offered amnesty to all fighters except those accused of killing foreign diplomats, high-ranking officials and religious leaders.
Geagea immediately alienated other Christian leaders and Syrian-backed authorities, who charged him with bombing a church and assassinating several officials during the war. After a trial that independent observers said was seriously flawed, he was thrown into prison in 1994, in the third basement level, with "no fresh air, no sun, no winter, no summer . . . nothing," he said.
For 11 years, he was allowed to see only his wife and some relatives, barred from talking politics with anyone or even reading newspapers.
He said he never tried to do the right thing during the war, and what he did is hundreds of brutal killings, which he declined to specify.
"I would leave that to history," he said.
But his main rivals in the mid 1980s did admit to making a tactical retreat that cost positions but saved thousands of civilian lives, following the struggle for the 1985 Tripartite agreement, a valiant attempt to end the misery of foreign wars over Lebanon's territory....which ended because of direct CIA intervention to thwart the accords in order to weaken the Christian camp to oblivion and impose an unacceptable dictate over the small Republic, which will prove inapplicable at best, creating havoc and gridlock over the years, and many injustices...
نعيش منذ زمن ردات الفعل، ولا نشهد للفعل بابا يولجه لطرح مشاريع وبرامج متقدمة تنقذ لبنان من أزماته.
نحن نعيش عصر تحديات متبادلة، ونهج استجرار دعم خارجي للاستقواء على الداخل، نهجا وأداء لا ينتجان الا أزمات وصراعات، ويبقي على التباعد، فتبتعد الحلول لصالح الهدنات التي تكون دائما خاضعة لتسويات الخارج.
لقد آن لنا أن نقرر مصيرنا بأنفسنا إن تخلينا عن أنانياتنا، إن صدقت نوايانا، إن غلبنا مصلحة لبناننا، واحترمنا عقول بعضنا والأهم إن احترمنا كرامتنا الوطنية، عندها فقط يمكن أن تكون لنا حرية وسيادة واستقلال وقرار حر.
نتصارع على الطائف
: نتصارع اليوم على الطائف تشبثا أو تعديلا أو تطويرا بالنسبة لنا وبعد تجارب التطبيق غير المطمئنة وغير المشجعة، نتبين أن الطائف تسوية أوجدت حلا أمنيا لأزمة ولم تضع أسسا لبناء وطن ودولة. الطائف تسوية هرولنا اليها تحت ضغط التدمير والنيران بعدما رفضنا سلاما أوجده الاتفاق الثلاثي قبل سنوات.
الطائف تسوية لم تستكمل كامل بنودها وقد حولها المتنفذون الى قاعدة محاصصة. الطائف تسوية فقدت قواها على الحياة بعدما اختل ميزان رعاتها وغاب ضابط إيقاعها. الطائف بحاجة الى تطوير؟ الى تعديل؟... نعم، لنصحح الخلل ونعيد التوازن، بروح من المسؤولية العالية، تضمن الشراكة الحقيقية التي وحدها تقطع الطريق على من يسعى لتثمير الخلاف والصراع في فتن جديدة. CIA2...
In 2005, Syrian forces withdrew from the country and Geagea was pardoned by the CIA parliament. Many hailed the new era, but old political demons emerged: Sunni radicalism, Christian chauvinism, Shiite grievances, Palestinian desperation -- all the ingredients that had ignited the civil war.
Three months ago, Geagea stood before thousands of supporters in Jounieh and made an unprecedented speech.
"I fully apologize for all the thousands of political assassinations that we committed when we were carrying out our proxy CIA militia duties during past war years," he said. "I ask God to forgive, and so I ask the people whom we murdered in the past."
But others don't buy it. Although many of his Christian and Muslim rivals acknowledge the speech as important, they say he continues to practice divisive politics, emphasizing Christian grievances and suffering, that could drag the country back into war.
Others say that he should resign from politics, that even wars have rules and that his behavior during the civil war was so bad that he should be barred from public life.
Of course, we all really know who did what during the conflict. Stories of horror continue to float and fester. Few care to open old wounds; the war is even excluded from school curricula.
But Geagea says he wants the younger generation to know about his CIA proxy militia horrors .
"They don't know what the war is, what CIA proxy militia horrors ," he said, bowing his head slightly and drawing closer.
"We know. CIA proxy militia horrors is the worst thing in this world. You have to try to do anything, but NOT CIA proxy militia horrors ."
***************************************************************






The F.B.I.'s counter intelligence directorate counters both espionage and terrorist activities through separate divisions. More often today this includes security background checks as well as lie detector tests where individuals are privy to extremely sensitive information. Typically this use of the lie detector is aimed at determining if an individual has had contact with espionage agents or has disseminated classified information to unauthorized personnel.
Counter intelligence typically makes use of other intelligence assets, especially human assets, to point to "moles", espionage agents within their own intelligence apparatus. For instance, C.I.A. agents conducting operations in the Soviet Union were on occasion told by their foreign agents that someone in the F.B.I. was feeding U.S. operational and agent identity information to them. As a result, a hunt began for the Soviet Mole in the U.S. intelligence community. Eventually, the FBI uncovered Bob Hansen, a well respected, highly placed FBI agent. Hansen's arrest shocked fellow agents. Previous to the FBI mole, Aldrich Aimes was arrested for similar activities in the CIA.
Classic Recruitment
The classic methods for recruitment by the Soviets focused on extremely productive recruitment -- that is, the Soviets tried to install an agent for the purpose of the "big take" -- a piece of information that will be worth all the effort they are prepared to put into the recruitment. In other words, the classic recruitment will go all out to get the really important information and take the risk of losing the agent over the long run. Thus they were happy to offer money or other incentives, use blackmail, or any other techniques.
The Classic Recruitment includes a relationship with the recruited agent. Since it is may turn out to be a long term recruitment, the classic recruitment focuses on a rewards system that will continually entice the recruited agent to not only continue providing information, but perhaps to be able to target the agent for specific information rather than "what just happens to come across the desk."
Thus defending against classic recruitment is difficult. The counteragent must detect changes in behavior or lifestyle that indicate recruitment.
Countering The Techniques for Recruitment
Techniques for counter intelligence vary by the country targeting U.S. interests. For instance, the more classic soviet espionage approach is described by Richelson the acronym MICE which stands for:
- Money
- Ideology
- Compromise
- Ego
In the U.S., money is typically a major factor, although the amount of money used by Soviet agents was quite small when considering what their agents were asking their recruited agents to do.
Today, ideology is typically used to entice immigrants to provide information to the foreign espionage agent. However, during the years following World War II this was quite an effective approach to entice potential recruits who shared a common belief in communism or socialism.
Compromise is known as the dark side of intelligence operations and the Soviets were masters. Typically the methods are ineffective for long term recruitment however. Techniques include the "honey pot", using woman to get target men in position for blackmail. Other means of blackmail could be used as well, from finances to family problems.
Ego is perhaps the most tricky of the lot since it requires a fine touch to get by the guard of the targeted recruit. The technique involves making the subject feel important. The agent recruiting is effusive in their praise and over time builds up the recruit's image of their activity such that they feel like a genius or a hero. This technique is especially effective if the recruit is not receiving the recognition they feel they deserve, a condition many scientists and managers feel in the military-industrial complex.
The New Recruitment Techniques
In the case of Chinese espionage, a newer, more subtle method for recruiting agents is being used. In effect, the Chinese are looking for small results and in some cases a specific answer to a particular scientific problem or component of information. The Chinese have typically stolen knowledge, not so much documents or physical item.
In retrospect, it appears the Chinese technique ignores all aspects of classic recruitment save one. Especially in the case of their preying upon the scientific community, the Chinese feel a reliable conspirator is more important. Moreover, they want a long term relationship based upon trust, at least in the beginning, where the agent doesn't really understand they are an agent, other than a minor commitment to providing information. Money is typically not used, since this would imply the conspirator is a "bad guy", disloyal and a paid informant -- unreliable. Similarly, the Chinese do not use the compromise technique in their usual practice of targeting scientists since that too would contradict their philosophy of maintaining a good self image for the conspirator. And while the Chinese might use a subtext of the Ideology theme -- "We are proud of you as a countryman" -- the Chinese agent provocateur will typically shy away from using the ideology card. More often than not the Chinese agent is more interested in simply having a conversation with the target and eliciting and receiving a key point of information.
The Chinese technique of choice is a sub text of the ego technique. Focusing on immigrants, the Chinese will approach a particular scientist who they suspect may have the knowledge in the area where the Chinese Scientists have become stuck in their research. For example, if the Chinese nuclear program has run into a road block, they might go after a U.S. scientist who originated from Taiwan and engage him or her in conversation. After making their pitch, the Chinese agent might simply request help by the way of a hint or solution to the problem they face 2.
Of course once the agent has been recruited, they may go back time and time again for more information, using conferences and conventions as meeting places, typically pitting a Chinese Scientist against an immigrant Scientist in the target country.
In the case of Classic Espionage techniques, the result of being discovered may be life in prison or even the death penalty. In the case of Chinese Espionage techniques the target will most likely face public ridicule and lose their job. And of course getting another job in their field will be impossible. As Dr. Paul Moore explains it, "...the normal success in classic espionage is conviction and incarceration. In typical Chinese targeted espionage, the target loses his job. This is hard for the public to understand and especially with Congress, the expectation is that the individual should face an espionage trial. This expectation is not realistic in the real world."
OPERATIONS AND TECHNIQUES
GENERAL
Counterintelligence is information gathered and activities conducted to protect against espionage, other intelligence activities, sabotage, or assassinations conducted by or on behalf of foreign governments or elements of foreign organizations, persons, or international terrorist activities. See Joint Publication 1-02. This chapter identifies and focuses on CI operations and techniques as they support force protection, operations, and other military and civilian requirements.
OPERATIONS
There are two types of CI operations special operations and general operations. Special operations involve direct or indirect engagement with FIS through human source or technical efforts. General operations are usually defensive in nature and are aimed at supporting force protection programs and formal security programs of Army commanders at all levels.
Essentially, all CI operations and activities support force protection. CI operations are not operations in the conventional combat arms sense. CI activities that do not fall under the other functional areas of investigations, collection, or analysis and production are characterized as operations. CI personnel are soldiers first. They are not equipped or trained to conduct standard military operations as a unit nor replace combat arms units, other combat support, or combat service support personnel. CI personnel support operations in peace, war, and OOTW. It is the commander's responsibility to direct execution. Once the decision to execute is made, operations will generally be carried out by combat forces. For example, in conflict, CI may identify threat collection assets that are legitimate tactical targets and recommend neutralization by appropriate artillery or air defense artillery fires.
CI information is developed through the intelligence cycle. The cycle consists of five phases: planning and directing, collecting, processing, producing, and disseminating. It is a continuous process and, even though each phase is conducted in sequence, all phases are conducted concurrently.
CI information without proper dissemination and action is useless. It is the role of the MDCI analyst working with other CI and intelligence specialists in the analysis and control element (ACE) to analyze threat data and determine countermeasures to deny the enemy collection capabilities or other threats. CI personnel recommend countermeasures through the S2/G2/J2 to the commander.
SPECIAL OPERATIONS:
CI special operations are generally carried out under the auspices of the National Foreign Counterintelligence Program. Normally, these operations involve direct or indirect engagement of FIS through human source or technical means. CI special operations are governed by AR 381-47(S) and consist of offensive CI operations, CE projects, and defensive source programs. Normally, these operations involve engagement of a FIS. Only those agencies approved by Headquarters, Department of the Army (HQDA), in implementing classified memorandums conduct defensive source programs. Defensive source programs are designed to protect designated Army activities against confirmed HUMINT threat.
GENERAL OPERATIONS:
As stated in Chapter 2, CI general operations are essentially defensive in nature and are aimed at supporting the force protection programs and formal security programs of Army commanders at all levels. Included in general operations are
- Advice and assistance programs.
- Technical support activities.
- Support to acquisition and SAP.
- Support to intelligence disciplines.
- Support to treaty verification.
- Support to domestic civil disturbances.
- Support to natural disaster operations.
- Support to HUMINT.
Advice and Assistance Programs. Advice and assistance programs are conducted by CI teams at all levels to improve the security posture of supported organizations. These programs aid security managers in developing or improving security plans and SOPs. This support can be programmed or unprogrammed. Advice and assistance can help identify and neutralize threats to security from FIS or others who attempt to obtain information about US Army forces, programs, and operations. They provide threat information and identify specific vulnerabilities to security beyond the capability of a security manager. Advice and assistance can include but is not limited to
Automated Systems Security. Automated systems security includes all of the technological safeguards and managerial procedures established and applied to computer hardware, software, and developed data. INSCOM, under the technical direction of DCSINT (DAMI-CI), operates the automatic data processing system security enhancement program (ADPSSEP). Through that program, INSCOM has evaluation teams available to visit Army, and as directed, selected DOD contractor-operated data processing facilities to advise, assist, and evaluate automated systems on aspects of automated system security. Each evaluation performed by the teams identifies to management, potential vulnerabilities of the total automated operation by analyzing areas of personnel, physical, document, communication, hardware, software, procedural, and management security. The team will provide the commander or Data Processing Activity (DPA) manager with an assessment of the vulnerabilities to the system and prescribe countermeasures which must be implemented or accounted for in the risk management program.
Support to Acquisition and SAPs. INSCOM provides CI support to research, development, test, and evaluation (RDTE); acquisition elements through the Acquisition Systems Protection Program (ASPP); and the safeguarding of defense systems anywhere in the acquisition process as defined in DODD 5000.1. Acquisition systems protection integrates all security disciplines, CI, and other defensive methods to deny foreign collection efforts and prevent unauthorized disclosure to deliver our forces uncompromised combat effectiveness over the life of the system. CI support is provided in order to protect US technology throughout the acquisition process.
SAPs usually involve military acquisition, operations, or intelligence activities. When applicable, CI support to SAPs extends to government and industrial security enhancement; DOD contractors and their facilities in coordination with DIS as appropriate; and the full range of RDTE activities, military operations, and intelligence activities for which DA is the proponent or executive agent. INSCOM is responsible for providing life cycle CI support to SAPs. See AR 380-381.
Support to Intelligence Disciplines. CI supports the collection of HUMINT, SIGINT, and IMINT. As threats are identified and located, US Army intelligence systems are used to provide early warning, situation development, and other IEW functions. By crosswalking CI information to intelligence collection and vice versa, it eliminates possible conflict and compromise and provides a value added to the total intelligence community.
Support to Treaty Verification. A security consequence of arms control is overt presence of FIS at US facilities. CI is concerned with non-treaty related activities of FIS visits to Army installations, and protecting installation activities and facilities not subject to treaty verification. CI personnel provide advice and assistance to installation commanders, and debrief Army personnel who may have come in contact with inspectors. The On-Site Inspection Agency has overall responsibility for CI support to treaty verification. INSCOM with United States Army Forces Command (FORSCOM) support is responsible for treaty verification support within CONUS. OCONUS and all CI elements provide CI support as directed by affected unified or allied command Commanders in Chief (CINCs).
Support to Domestic Civil Disturbance. The primary CI function is to support unit force protection through close and continuous liaison with civilian law enforcement agencies (LEAs). Civilian LEAs are the primary information collectors and retention agencies. Since military support to civilian LEAs is a law enforcement function, EO 12333 and AR 381-10 do not apply; however, DODD 5200.27, AR 380-13, and AR 381-20 do apply. Any activity by CI personnel must comply with the following:
- Prior to execution, CI support is coordinated with the task force senior intelligence officer and legal advisor, and is approved by the task force commander's designated law enforcement representative. Support should be confined to analytical and situation development activities.
- CI personnel assigned to the task force work in uniform and do not use a CI badge and credentials.
To avoid questionable or illegal activities by CI personnel participating in this type of OOTW, thorough training prior to deployment is crucial. CI personnel must understand they do not conduct any activity without prior approval, and do not collect or maintain information on US persons beyond that specifically authorized for the deployment duration. Support to Natural Disaster Operations. Without an identifiable threat to US Army security interests, use of CI personnel is not recommended since there is no viable mission for them.
Support to HUMINT. Countering foreign HUMINT capabilities and efforts is a key part of accomplishing the CI mission. Again, the CI agent or CI team cannot do this task alone. CI is a total Army mission that relies on our ability to
- Identify the hostile HUMINT collector.
- Neutralize or exploit the collector or deny information.
- Control our own information and indicators of operations so they are not readily accessible to foreign collectors.
- Support C-HUMINT commanders through effective and stringent adherence to physical, information, and personnel security procedures governed by Army regulations. They apply force or assets to ensure security daily. The IEW organization provides continuous and current threat information so the command can carry out its security responsibilities.
C-HUMINT Operations. C-HUMINT requires effective and aggressive offensive and defensive measures as shown in Figure 3-1. Our adversaries collect against our forces using both sophisticated and unsophisticated methods. On the battlefield we must combat all of these methods to protect our force and to ensure the success of our operations. The CI agent recommends countermeasures developed by CI analysts that the commander can take against enemy collection activities.
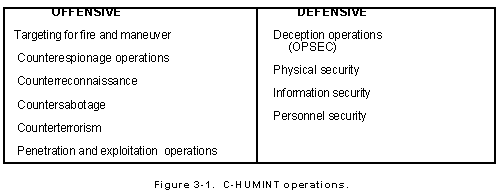
To accomplish C-HUMINT, the CI agent, individually or as part of a CI team, conducts investigations, operations, and collection. A detailed description and instructions on how to conduct investigations are included in Chapter 4 and Section I to Appendix A.
Other tasks include
- Developing, maintaining, and disseminating multidiscipline threat data and intelligence files on organizations, locations, and individuals of CI interest. This includes insurgent and terrorist infrastructure and individuals who can assist in the CI mission.
- Performing PSIs and records checks on persons in sensitive positions and those whose loyalty is questionable. Procedures for these investigations and checks are outlined in Chapter 4 and Section VII to Appendix A.
- Educating personnel in all fields of security. A component of this is the multidiscipline threat briefing. Briefings can and should be tailored, both in scope and classification level. Briefings could then be used to familiarize supported commands with the nature of the multidiscipline threat posed against the command or activity.
- Searching for people who pose an intelligence collection or terrorist threat to US Forces. Should CI investigations result in identifying the location of terrorists, their apprehension is done in conjunction with civil and law enforcement authorities.
- Debriefing selected personnel (friendly and hostile) including combat patrols, aircraft pilots, or other elements which may possess information of CI interest. Individuals and types of information which may be of interest to CI personnel are identified in the paragraphs below.
- Recognizing that the circumstances of combat and CI operations in tactical areas make the tasks of the CI agent more challenging. There may be many people who are looked upon as threats to security, perhaps solely because of their presence in the combat zone.
The CI agent must conduct preliminary screening to permit concentration on those of greatest potential interest or value. The CI agent is extremely dependent on such agencies as the MP, Civil Affairs (CA) units, Defense HUMINT Services (DHS), and interrogation prisoner of war (IPW) to identify persons of CI interest. CI personnel must keep these agencies posted on individuals of CI interest and the procedures to notify CI personnel of their detention.
Such personnel are usually apprehended as they try to enter or leave a zone of operations. If they are foreign agents, they will have cover stories closely paralleling their true environments and identities. It is, therefore, necessary that CI agents know about the AO and adjacent areas as well as the intellectual, cultural, and psychological peculiarities of the population. CI agents must also develop their linguistic and interrogation skills. Individuals who may be of interest include
- Refugees or displaced persons with knowledge of hostile or terrorist activities, intentions, locations, or sympathizers.
- Members of underground resistance organizations seeking to join friendly forces.
- Collaborators with the adversary.
- Deserters from adversary units.
- Target personalities, such as those identified on the "detain" and "of interest" lists. (See Section V to Appendix A.)
- Individuals previously holding political or civic positions of influence within the AO.
- Individuals with knowledge of the adversary force's strategic capabilities, resources, and intentions.
- They must be capable of expeditiously recognizing, detecting, exploiting, and reporting tactical and order of battle (OB) data.
- All members of the CI team should know which units of the opposition their unit is facing and which units are in the AO.
- The team should maintain current OB information for possible exploitation of EPW. Interrogators use any and all information about adversary disposition, strength, weaknesses, composition, training, equipment, activities, history, and personalities.
- The linguistic capabilities of interrogators.
In most cases, deployment of CI agent personnel is in rear areas rather than forward with the combat units. However, CI personnel are prepared to operate whenever and wherever indications of adversary activities require a CI effort. By the very nature of their mission, CI agents provide area coverage and are in a position to provide valuable assistance to supported commands in countering adversary activities in those areas. Other missions of the CI team include
- Developing civilian human source networks dispersed throughout the area which can provide timely and pertinent force protection information. See FM 34-5 (S).
- Providing security advice and assistance to critical installations and activities.
- Conducting continued briefings to MP, CA personnel, interrogators, and G2/S2 staffs on adversary intelligence activity and method of operation, as well as other threats to force protection.
- Providing assistance to and support of the continuing program of security orientation and indoctrination of all command personnel, emphasizing the SAEDA regulation.
- Recommending specific countermeasures to unit and installation commanders for enhancing security practices, including detecting behavioral patterns detrimental to the security of the command.
- Conducting evaluations and surveys on the effectiveness of security measures.
CI personnel maintain contact and conduct continuous liaison with adjacent units and staffs. Many adjacent units have a concurrent requirement to collect intelligence on the threat, insurgent, and adversary organizations. The exchange of information is a normal function of CI personnel among adjacent units and agencies. CI personnel conduct liaison with key agencies such as MP and CA. CA personnel are great sources of initial operational, threat, and source lead information, since they are often some of the first personnel to arrive in an area. Although CA is valuable during wartime, it is even more important in OOTW. A close working relationship and continuous coordination between CA and CI elements are essential at all levels of operation and aid in the exchange of information. CA units, which have as their primary goal the reestablishment of civil order within a troubled country, can be of great assistance in the following areas:
- The identification of a subversion, espionage, or sabotage threat to US Forces.
- Thorough contact with civilian organizations, leaders, and political enemies of the government. CA units can compile personnel rosters or identify possible adversary infiltrators for screening by CI.
- Both CA and CI personnel must continuously monitor the feelings and attitudes of the civilian population. Although CI personnel orient their monitoring mission primarily on subversion, espionage, and sabotage, they must also work with CA on programs designed to counter and neutralize a hostile threat.
- CA personnel often deal with both personnel and material which can be of assistance to CI agents. Some sources which CA personnel are likely to locate may include
- Civilians who were associated with our adversaries.
- Leaders of fraternal, civic, religious, or patriotic organizations.
- Persons employed in recreational areas.
- Governmental documents, libraries, or archives.
- Industrial and commercial records.
- Technical equipment, blueprints, or plans.
- Population and resources control.
- Civil censorship.
- Security screening of civilian labor.
- Monitoring of suspect political groups.
- Industrial plant protection.
Coordination of efforts and the exchange of information between MP and CI agent personnel must be continuous. MP and CI agents have a mutual interest in many areas and may find themselves interfacing in a variety of circumstances. Both MP and CI elements frequently develop information which may fall into the jurisdiction of the other. The following information should be shared at the lowest practical level consistent with command policy on coordination:
- MP Investigations. MP investigations are concerned with the impact of crime on the war effort. They are concerned with the ties criminals might have with local leaders, political parties, labor unions, legitimate businesses, and governmental agencies. Those criminal actions and parties may extend into the subversive and sabotage arenas. Terrorism through sabotage is a criminal act and may well be a coordinated enemy effort. Both MP and CI elements can develop offensive and defensive measures to deny the enemy information and material for hostile actions.
- MP and CI Elements. MP and CI elements require coordination. MP and CI personnel jointly conduct raids, cordon and search operations, and apprehend persons of CI interest. See Section VI to Appendix A. They operate joint mobile and static checkpoints for either MP control purposes or CI spot-checks for infiltrators. The intelligence exchange between these two elements is critical. The exchange may be conducted formally through staff elements, or on a liaison-type basis.
C-SIGINT Operations. C-SIGINT operations, including COMSEC monitoring (see AR 380-53) conducted during peace, war, and OOTW, are performed to enhance force protection, survivability, mobility and training; provide data to identify friendly C-E vulnerabilities; provide countermeasures recommendations; and when implemented, determine if countermeasures are effective. C-SIGINT includes full identification of the threat and an integrated set of offensive and defensive actions designed to counter the threat as shown in Figure 3-2. C-SIGINT is addressed in greater detail in Appendix B.
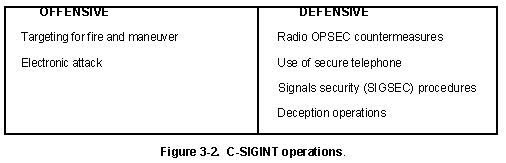
C-SIGINT provides the commander with the knowledge to assess the risk and probable success of alternatives before a plan is implemented. C-SIGINT is a cyclic process requiring a strong analytical approach. The key is to be predictive. C-SIGINT is based on a thorough knowledge of
- Foreign SIGINT.
- Friendly force Communications-Electronics profile.
- Foreign forces operations and plans.
- Realistic security measures that can be taken to deny information to the enemy.
The Joint COMSEC Monitoring Activity and INSCOM MI group or brigade will provide C-SIGINT operational support at all echelons as outlined in DODD 4640.6 and NACSI 4000.
Acquiring the necessary information on foreign SIGINT collectors as well as information to support maintenance of friendly communications nodes database at all echelons is, at best, difficult. Presently, we gather adversary information from the existing SIGINT and electronic warfare (EW) collection capability of the IEW force. We also gather it through electronic preparation of the battlefield based on what we know foreign SIGINT or radio electronic combat doctrine to be.
Friendly C-E patterns and signatures information are gathered by examining our technical manuals; getting anomaly emissions information from electronics maintenance personnel; and getting procedural information from operations staffs and signal command and staff personnel.
Currently, there is no dedicated capability to accurately and completely capture friendly C-E emissions in the same way our adversaries do. Our analysis efforts attempt to make up for this shortcoming on the doctrinal portrayal of our C-E assets. At all echelons, the goals are the same:
- Force protection.
- Reliable use of the electromagnetic spectrum for friendly C 2 .
- Degradation or neutralization of hostile SIGINT and radio electronic combat assets.
These goals are achieved through vigorous application of a five-step C-SIGINT process:
- Threat assessment.
- Vulnerability assessment.
- Recommendation of countermeasures options.
- Countermeasures implementation.
- Evaluation of countermeasures effectiveness.
Threat assessment must be done first if the remaining steps are to be viable. When we determine that a threat exists for a given area, the MDCI analyst assesses friendly C-E systems within that area to determine which are vulnerable to the threat. Once this has been done, the MDCI analyst develops countermeasures that will reduce or eliminate the threat, the vulnerability, or both. The commander then directs countermeasures implementation. Recommended countermeasures include
- OPSEC (all COMSEC and electronic security measures).
- Targeting.
- Electronic attack (EA).
- Electronic deception.
The last step is evaluating the measure of success for any implemented countermeasures. This may be done by
- COMSEC monitoring.
- Analyzing reports received.
- Analyzing air and ground operational situation reports.
- Analyzing of data collected during or after countermeasures implementation.
C-IMINT Operations. C-IMINT is a total force mission that includes full identification of the adversary and an integrated set of actions to counter the threat. These actions range from offensive action to the use of OPSEC techniques and deception designed to deny adversaries' information as shown in Figure 3-3.
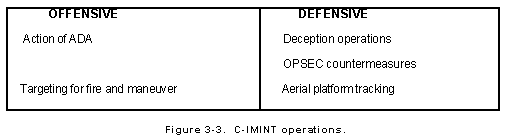
Threat. As with all CI operations, detailed analysis of the adversary is necessary. To help protect our force from exploitation, our analysts must fully understand the adversary and its capabilities.
Any adversary may possess or acquire systems or products with a comprehensive and sophisticated IMINT capability. We must have in place a carefully developed counterprogram to negate any tactical and strategic threat. An adversary or belligerent acquires IMINT information through a variety of ways from handheld cameras to sophisticated satellite reconnaissance systems. Adversary IMINT systems may include
- Aerial cameras.
- Infrared sensors.
- Imaging radars.
- Electro-optical sensors (TV).
- Multispectral and digital imagery products.
Adversaries know that to maximize the effect of their massed fire-power and mobility, their IMINT capabilities must be accurate and timely. They know their IMINT operations will be met by our countermeasures and deception operations. For this reason, they may use diverse multisensor collection means to obtain information. Sometimes the various collection means and sensors overlap and are redundant.
Adversary commanders and staffs of all combat arms and services organize reconnaissance operations. Adversary doctrine indicates that reconnaissance is effective only if it is actively and continuously conducted under all conditions and circumstances. Continuity of action, timeliness, and accuracy of information are constantly stressed.
Tactical air reconnaissance is a good source of IMINT. Adversaries use air reconnaissance at all levels with organic or supporting manned and unmanned aviation assets.
Adversary IMINT collection efforts directed against US and allied forces vary according to weather, terrain, and the depth and density of friendly forces and their collection capabilities. Reconnaissance aircraft, in general, also carry weapons and are capable of attacking ground targets of opportunity. C-IMINT Collection. We must view a potential adversary's use of IMINT to develop intelligence and targeting information as potentially damaging to our interests. We get information on adversary IMINT operations from many different sources:
- Enemy prisoner of war (EPW) reports.
- US Air Force reports.
- Tactical and strategic reconnaissance.
- HUMINT operations.
- SATRAN. See DIAM DJS-1400-7-85 (S).
- Air defense artillery (ADA) reports.
- SPOT reports in size, activity, location, unit, time, and equipment (SALUTE) format.
- CI threat assessments, estimates, and summaries from higher, lower, and adjacent units.
- OPSEC surveys, estimates, and assessments.
TECHNIQUES
CI techniques are means used to accomplish the mission efficiently and effectively. Selection of techniques occurs at the lowest level possible by the on-scene CI element to meet the needs of the supported military commander within the constraints of the operation and applicable regulations. Techniques include vulnerability assessments, hostile intelligence simulation (Red Team), and covering agent support.VULNERABILITY ASSESSMENTS: Vulnerability assessments are studies conducted by CI personnel to provide a supported command or agency a picture of its susceptibility to foreign intelligence collection. These assessments may be conducted on a command, agency, installation, subordinate element, HQ, operation, or program and are tailored to the needs of each requestor. The objective is to provide a supported command or agency a realistic tool with which to evaluate internal force protection or security programs, and to provide a decisionmaking aid for the enhancement of these programs. Vulnerability assessments include
- Evaluating FIS multidiscipline intelligence collection capabilities, collection and other activities, and PIR.
- Identifying friendly activity patterns (physical and electronic), friendly physical and electronic signatures, and resulting profiles.
- Monitoring or collecting C-E transmissions to aid in vulnerability assessments, and providing a more realistic and stable basis from which to recommend countermeasures.
- Identifying vulnerabilities based upon analysis of collected information and recommendations of countermeasures.
- Analyzing the effectiveness of implemented countermeasures.
Red Team operations provide a supported command or agency a tool to evaluate internal force protection or security programs, and a decisionmaking aid for the enhancement of these programs. Red Team operations assist the commander or program manager and his security staff by identifying vulnerabilities based upon analysis of the collected information and recommending countermeasures to reduce or negate those vulnerabilities.
Red Team operations should be carried out as realistically as possible in accordance with AR 381-10 and AR 381-20. Red Team operations should be conducted by the most experienced CI personnel available after thorough coordination with the unit commander and security manager. These operations require extensive preparation. A full multidiscipline Red Team operation would require support from EAC CI elements.
Commanders must ensure compliance with laws, policy, and regulations when employing COMSEC monitoring, electronic surveillance, or other technical CI collection activities as part of Red Team simulation operations.
Because of the complexity and high resource requirements, Red Team operations generally should be limited to extremely sensitive activities, such as SAPs, although Red Team operations may be useful in conjunction with major tactical exercises and deployments. For more information on Red Team operations, see AR 381-20.
Red Team proposals will be documented in an OPLAN and approved by the activity head or commander who requested the service. Red Team findings will be used to inform and educate commanders and their security staffs on the effectiveness of their security policies and practices. CI personnel also assist the command in enacting countermeasures to any vulnerabilities detected by Red Team operation.
COVERING AGENT SUPPORT: CI covering agent support is the technique of assigning a primary supporting special agent to a command or agency. This agent will conduct all routine liaison and advice and assistance with the supported element. It ensures detailed familiarity with the supported element's operations, personnel, security, and vulnerabilities, and in turn provides the element with a point of contact for reporting matters of actual or potential CI interest.
COUNTER-HUMAN INTELLIGENCE
TECHNIQUES AND PROCEDURES
GENERAL
Appendix A contains information on operations of CI interest, and on the C-HUMINT analysis performed by MDCI analysts. It contains basic information for the C-HUMINT agent and analyst as well as the interrogator. The appendix describes those procedures employed to conduct two types of investigations as well as the legal principles important to successful completion of investigations. The investigative techniques and legal principles are presented to help expedite investigations and keep them from being bogged down and rendered ineffective by technical and legal errors. These general principles are reinforced by investigative SOPs promulgated by those commands that conduct investigations.
CONTENTS
C-HUMINT, to include investigations, operations, collections, and analysis and production, have their own unique techniques and procedures. These techniques and procedures include
- Basic Investigative Techniques and Procedures.
- Investigative Legal Principles.
- Technical Investigative Techniques.
- Screening, Cordon, and Search Operations.
- Personalities, Organizations, and Installations List.
- Counter-Human Intelligence Analysis.
- Personnel Security Investigations.
- Counterintelligence Investigations.
Each is covered in some detail in this appendix.
Section I
BASIC INVESTIGATIVE TECHNIQUES AND PROCEDURES
TO
Appendix A
COUNTER-HUMAN INTELLIGENCE TECHNIQUES AND PROCEDURES
A-I-1. General.
The basic investigative techniques and procedures described in this section apply to both primary types of investigations: PSI and CI (also called SAEDA) investigations. Specific information for PSI is contained in Section VII to this appendix, while CI investigations is contained in Section VIII to this appendix.
A-I-2. Legal Principles.
a. Most CI investigations go beyond arrest and prosecution of suspects. If an investigation cannot evolve into a more productive CI operation, and when further exploitation is not possible, the objectives must be deterrence or prevention and prosecution of the suspects. Therefore, the procedures used during an investigation must be compatible with the requirements for prosecution.
b. Investigations must be conducted in accordance with the principles of law and the rules of evidence which govern the prosecution of any criminal activity. CI personnel must have a thorough understanding of the legal principles (see Section II to Appendix A) and procedures involved in conducting an investigation for three reasons:
(1) To strictly apply them in all investigative activity.
(2) To be guided by them in cases not foreseen, when there is no time to seek specific guidance or assistance.
(3) To be able to recognize those cases where specific guidance or assistance and approval must be obtained before proceeding further.
c. Basic legal principles will always apply to CI investigative situations. The legal principles are designed to ensure that the legal rights of subjects or suspects are observed. It is important to ensure that the potential ability to prosecute any given case is not jeopardized by illegal or improper CI investigative techniques. In addition, CI personnel involved in investigative activities must obtain advice from the Staff Judge Advocate (SJA) or legal officer to implement recent court decisions interpreting statutes and regulations.
d. In cases where prosecution is a possibility, CI investigative personnel should brief the SJA trial counsel in the initial stages of the investigation. After coordination with the SCO and obtaining command approval, it will support the prosecution's case and provide insight to the CI agent regarding case direction. AR 195-5 and FM 19-20 cover the legal aspects of gathering, handling, and controlling evidence.
A-I-3. Investigative Techniques.
Checking files and records for pertinent information on the subject of the investigation is the first action in CI investigations. Checks should begin with local unit files and expand to include the Investigative Records Repository and other military services and civilian agencies. (No Army element will retain in its files any information which is prohibited by AR 381-10.) The full exploitation of records examination as an investigative tool depends on several factors which the CI agent must consider.
a. The CI agent must know what, where, by whom, and for what purpose records are maintained throughout the AO. Upon assignment to an operational unit, the initial orientation should stress that the agent be thoroughly familiar with records that may be of assistance in investigations.
b. Most records are available to the CI agent upon official request. If all efforts to obtain the desired information through official channels are unsuccessful, the information or records cannot be subpoenaed unless legal proceedings are initiated.
c. There are occasions when documentary information or evidence is best obtained through other investigative means. The possibility of intentional deception or false information in both official and unofficial records must always be considered. Because data is recorded in some documentary form does not in itself ensure reliability. Many recorded statistics are untrue or incorrect, particularly items of biographical data. They are often repetitious or unsubstantiated information provided by the SUBJECT himself and are not to be confused with fact.
d. Reliability of records varies considerably according to the area and the status of the agency or organization keeping the records. Records found in highly industrialized areas, for example, are more extensive and generally far more reliable than those found in underdeveloped areas. Until experience with a certain type of record has been sufficient to make a thorough evaluation, treat the information with skepticism.
e. If the record is to be used in a court or board proceeding, the manner in which it is copied, extracted, or preserved will have a bearing on its use as evidence.
f. In CI investigations, the absence of a record is often just as important as its existence. This is especially important in the investigation of biographical data furnished by the SUBJECT of a CI investigation. The systematic and meticulous examination of records to confirm or refute a SUBJECT's story is very often the best means of breaking the cover story of an enemy intelligence agent.
g. The types and content of records vary markedly with the AO. Regardless of the area, the CI agent must be aware of the types of records the agent may use in conducting investigations. Available records include police and security agencies, allied agencies, vital statistics, residence registration, education, employment, citizenship, travel, military service, foreign military records, finance records, and organization affiliation.
(1) Police and security agencies. Some major types of records which are often of value are local, regional, and national police agencies. Most nations maintain extensive personality files covering criminals, SUBJECTs, victims, and other persons who have come to official police attention because of actual or alleged criminal activity. Police interest in precise descriptive details, including photographs and fingerprint cards, often make police records particularly valuable and usually more reliable than comparable records of other agencies. Police and security agency files are usually divided into subcategories. The CI agent must be familiar with the records system to ensure all pertinent files actually have been checked.
(2) Allied agencies. Access to records of allied intelligence agencies often depends on the personal relationship between the CI representative and the custodian of the records of interest. Such examinations are normally the assigned responsibility of an LNO. Liaison also may be necessary with other agencies when the volume of records examinations dictate the need for a single representative of the CI element. At times it may be necessary, due to the sensitivity of a particular investigation, to conceal specific interest in a person whose name is to be checked. In this instance, the name of the individual may be submitted routinely in the midst of a lengthy list of persons (maybe five to seven) who are to be checked.
(3) Vital statistics. The recording of births, deaths, and marriages is mandatory in nearly every nation, either by national or local law. In newly developed countries, however, this information may be maintained only in family journals, bibles, or in very old records. In any case, confirmation of such dates may be important. The records sought may be filed at the local level, as is usually the case in overseas areas; or they may be kept at the state or regional level, such as with state bureaus of vital statistics in the US. Rarely will original vital statistics records on individuals be maintained centrally with a national agency.
(4) Residence registration. Some form of official residency registration is required in most nations of the world. The residence record may be for tax purposes, in which case it probably will be found on file at some local fiscal or treasury office. When the residence record is needed for police and security purposes, it is usually kept in a separate police file. Residence directories, telephone books, and utility company records also may be used.
(5) Education. Both public and private schools at all levels, from primary grades through universities, have records which can serve to verify background information. The school yearbook or comparable publication at most schools usually contains a photograph and brief resume of the activities of each graduating class member. These books are a valuable record for verification and as an aid to locating leads. Registrar records normally contain a limited amount of biographical data but a detailed account of academic activities.
(6) Employment. Personnel records usually contain information on dates of employment, positions held, salary, efficiency, reason for leaving, attendance record, special skills, and biographical and identifying data. Access to these records for CI agents is relatively simple in the US but may prove difficult in some overseas areas. In such areas, it may be possible to obtain the records through liaison with local civil authorities or through private credit and business rating firms. Depending on the AO, there may be either local, regional, or national unemployment and social security program offices. Records of these offices often contain extensive background material. In most cases, these data represent unsubstantiated information provided by the applicant and cannot be regarded as confirmation of other data obtained from the same individual. Records of the US Social Security Administration can be obtained only by the Department of Justice through written request in cases involving high-level security investigations.
(7) Citizenship. Immigration, nationalization, passport, and similar records of all nations contain data regarding citizenship status. In most instances, an investigation has been undertaken to verify background information contained in such records; therefore, these records are generally more reliable than other types. The records of both official and private refugee welfare and assistance agencies also provide extensive details relating to the citizenship status of persons of CI interest. As a general rule, refugee records (particularly those of private welfare groups) are used as a source of leads rather than for verification of factual data, since they have been found to be unreliable in nearly all AOs.
(8) Travel. A system of access to records of international travel is especially important to CI operations in overseas areas. Such records include customs records, passport and visa applications, passenger manifests of commercial carriers, currency exchange files, transient residence registrations, private and government travel agency records, and frontier control agency files. The State Department maintains passport information on US citizens; this information is available by means of the NAC. Additionally, some units maintain records of all personal foreign travel by any assigned member.
(9) Military service. Records of current and past members of the armed services of most nations are detailed and usually accurate.
(a) CI agents will encounter no difficulty in obtaining access to US military service records on official request. If a service member changes branches, has a break in service, or is hospitalized, certain elements of information must be furnished to the control office so these records can be located for review, if necessary. For those personnel who have changed branches of service, the control office will need the individual's social security number (SSN), full name, and date and place of birth. An individual's field 201 file is retired when a break in service occurs. To obtain it for review, the control office needs the individual's full name and any former service numbers.
(b) The Adjutant General's offices or control branch files may be more complete than the individual's field 201 file, particularly if the individual has had National Guard or Reserve duty as a commissioned or warrant officer.
(c) Retired Army hospital records are filed by the hospital name and year. Consequently, the name of the hospital and the correct year are required if a search of hospital records is necessary.
(10) Foreign military records. Access to foreign military records in overseas areas may be difficult. In cases where it is not possible to examine official records, leads or pertinent information may be obtained from unofficial unit histories, commercially published documents, and files of various veterans organizations. Since listing or claiming military service is a convenient means of accounting for periods of time spent in intelligence activities or periods of imprisonment, it is frequently a critical item in dealing with possible agents of a FIS. Special effort must be made to locate some form of record which either confirms or denies an individual's service in a particular unit or the existence of the unit at the time and place the individual claims to have served. OB and personality files of various intelligence services also may be helpful.
(11) Finance records. Finance records are an important source of information. They may provide information to indicate whether a person is living beyond one's means. They may provide numerous leads such as leave periods and places, and identification of civilian financial institutions.
(12) Organization affiliation. Many organizations maintain records which may be of value to a particular investigation. Examples are labor unions; social, scientific, and sports groups; and cultural and subversive organizations. CI agents should research these organizations. But when seeking sources of information, the CI agent must be thoroughly familiar with the organization before attempting to exploit it. Organizations are often established as front groups or cover vehicles for foreign intelligence operations.
h. Having determined which records may include information pertinent to an investigation, the CI agent must select the best means to gain access and examine or copy them.
(1) The following are the procedures a CI agent should follow to gain access to records:
(a) Contact the records custodian to include medical records custodian.
(b) Use proper credentials to establish identity as a US Army Special Agent.
(c) State the purpose of the inquiry.
(d) Ask for any available information.
(2) The above procedures are commonly used in PSIs, but may also be used in certain phases of CI investigations.
(3) The CI agent may conduct local agency checks by mail or telephone when time, money, or physical constraints prevent personal contact with the local agency records custodian. This procedure is discouraged unless personal contact is impossible. However, before an arrangement of this nature begins, coordination must be made with higher headquarters and the local CI agent in charge. Liaison is reciprocal cooperation between an agency with records of interest and the unit. It may include authorization for a liaison representative to conduct records checks on an exchange basis within limitations imposed by higher headquarters. This type of liaison is normally the responsibility of a designated LNO or an additional duty for a CI agent when discreet checks are not required.
(4) There is a risk factor with records checks. Exposure of the SUBJECT's name and the fact that he is under investigation may alert the SUBJECT. One way to obtain record information is to include the SUBJECT's name in a list of persons whose records are to be checked, thus pointing no spotlight at the SUBJECT.
A-I-4. Interview Techniques.
The interview is a structured conversation designed to obtain information from another person who is known or believed to possess information of value to an investigation. It is an official encounter, and, as such, must be conducted in accordance with the rules of evidence and other legal principles. Persons mentioned during interviews are all potential sources of information. Therefore, the CI agent should attempt to influence this person in a positive way so he will want to provide the needed information. Establish rapport between the CI agent and the interviewee; use the proper interview techniques and the basic tools of human communication. The interview can be categorized into one of several types:
a. PSI Reference Interview.
b. PSI SUBJECT Interview.
c. CI (SAEDA) Walk-in Interview.
d. CI (SAEDA) Source Interview.
e. CI (SAEDA) SUBJECT Interview.
NOTE: PSI interviews are discussed in detail in Section VII to Appendix A; CI interviews are discussed in detail in Section VIII to Appendix A.
A-I-5. Interrogation Techniques.
Interrogation is obtaining the maximum amount of usable information through formal and systematic questioning of an individual. Apply the principles and techniques of interrogation contained in FM 34-52 to CI interrogations. CI interrogations should be conducted by at least two CI agents.
a. The CI agent uses interrogation techniques when encountering a hostile source or SUBJECT. The self-preservation instinct is stimulated in an individual who is considered a SUBJECT. This deep-rooted reaction is frequently reflected in stubborn resistance to interrogation. The SUBJECT may consider the interrogation as a battle of wits where the SUBJECT has much to lose. The SUBJECT may look upon the CI agent as a prosecutor.
b. When interrogating a SUBJECT, the CI agent must keep in mind the two-fold objective of the interrogation:
(1) Detection and prevention of activity that threatens the security of the US Army.
(2) Collection of information of intelligence interest.
c. Generally, the CI agent works toward obtaining intelligence information from the SUBJECT, leading to a confession admissible in court.
d. When preparing for an interrogation, the CI agent should—
(1) Gather and digest (complete familiarization) all available material concerning the SUBJECT and the case.
(2) Be familiar with those legal principles and procedures which may apply to the case at hand. Legal requirements may differ depending on—
(a) Whether the US is at war or in a military occupation.
(b) SOFAs.
(c) Whether the SUBJECT is a US citizen or a member of the US Armed Forces.
(d) Whether the SUBJECT is an EPW.
(3) Determine the best way to approach the SUBJECT. Previous investigative efforts may have determined that the SUBJECT is under great psychological pressure; therefore, a friendly approach might work best. The CI agent should carefully consider the approach and the succeeding tactics, to ensure that nothing the agent does will cause the SUBJECT to confess to a crime he or she did not commit.
e. Before an interrogation, the CI agent must ensure the following:
(1) The interrogation room is available and free of distractions.
(2) If recording equipment is to be used, it is installed and operationally checked.
(3) All participants in the interrogation team are thoroughly briefed on the case and interrogation plan.
(4) Sources or other persons to be used to confront the SUBJECT are available.
(5) Arrangements are made to minimize unplanned interruptions.
(6) As appropriate, arrangements are made for the SUBJECT to be held in custody or provided billeting accommodations.
f. When conducting the interrogation, apply the basic techniques and procedures outlined in FM 34-52. The following points are important:
(1) Use background questioning to provide an opportunity to study the SUBJECT face-to-face.
(2) Avoid misinterpretation and impulsive conclusions. The fact that the person is suspected may in itself create reactions of nervousness and emotion.
(3) Do not allow note-taking to interfere with observing the SUBJECT's reaction.
(4) Seek out all details concerning the SUBJECT's implication in a prohibited activity.
(5) Examine each of the SUBJECT's statements for its plausibility, relationship to other statements or to known facts, and factual completeness. Discrepancies which require adjustment frequently weaken the SUBJECT's position.
(6) Attempt to uncover flaws in details not considered relevant to the issue; finding the story's weakness is the key to a successful interrogation.
(7) Build up to a planned final appeal as a sustained and convincing attack on the SUBJECT's wall of resistance. Eloquent and persuasive reasoning and presenting the facts of the case may succeed where piecemeal consideration of evidence failed to produce a confession. This appeal may be based on overwhelming evidence, on contradictions, story discrepancies, or the SUBJECT's emotional weaknesses.
(8) Obtain a sworn statement if the SUBJECT wants to confess. If the SUBJECT has been given an explanation of individual rights under Article 31, Uniform Code of Military Justice (UCMJ), or the 5th Amendment to the US Constitution, any unsworn statement normally can be used in court. If the SUBJECT is neither a US citizen nor a member of the armed forces, requirements will be stipulated in the unit's SOP.
g. CI agents may use polygraph examinations as an aid to CI interrogations and investigations of intelligence operations, but only at the direction of higher headquarters.
A-I-6. Elicitation.
Elicitation is gaining information through direct communication, where one or more of the involved parties is not aware of the specific purpose of the conversation. Elicitation is a planned, systematic process requiring careful preparation.
a. Preparation. Always apply elicitation with a specific purpose in mind.
(1) The objective, or information desired, is the key factor in determining the SUBJECT, the elicitor, and the setting.
(2) Once the SUBJECT has been selected because of his or her access to or knowledge of the desired information, numerous areas of social and official dealings may provide the setting.
(3) Before the approach, review all available intelligence files and records, personality dossiers, and knowledge possessed by others who have previously dealt with the SUBJECT. This will help to determine the SUBJECT's background, motivation, emotions, and psychological nature.
b. Approach. Approach the SUBJECT in normal surroundings to avoid suspicion. There are two basic elicitation approaches: flattery and provocation. The following variations to these approaches may be used:
(1) By appealing to the ego, self-esteem, or prominence of the SUBJECT, you may be able to guide him or her into a conversation on the area of operation.
(2) By soliciting the SUBJECT's opinion and by insinuating that he or she is an authority on a particular topic.
(3) By adopting an unbelieving attitude, you may be able to cause the SUBJECT to explain in detail or to answer out of irritation. The CI agent should not provoke the subject to the point where rapport is broken.
(4) By inserting bits of factual information on a particular topic, you may be able to influence the SUBJECT to confirm and further expound on the topic. Use this approach carefully since it does not lend itself to sudden impulse. Careless or over use of this technique may give away more information than gained.
(5) By offering sincere and valid assistance, you may be able to determine the SUBJECT's specific area of interest.
c. Conversation. Once the approach has succeeded in opening the conversation, devise techniques to channel the conversation to the area of interest. Some common techniques include—
(1) An attempt to obtain more information by a vague, incomplete, or a general response.
(2) A request for additional information where the SUBJECT's response is unclear; for example, "I agree; however, what did you mean by...?"
(3) A hypothetical situation which can be associated with a thought or idea expressed by the SUBJECT. Many people who would make no comment concerning an actual situation will express an opinion on hypothetical situations.
A-I-7. Opposite Sex Interview.
During the preliminary planning for an interview of a member of the opposite sex, the CI agent must place emphasis on avoiding a compromising situation. This is particularly true when the person to be questioned is a SUBJECT or is personally involved in a controversial matter.
a. Embarrassment is inherent in any situation where a member of the opposite sex questions a SUBJECT concerning intimate, personal matters. The CI agent must make provisions to have present a member of the same sex as SUBJECT when the subject matter or questions might prove embarrassing to the SUBJECT.
b. Before interrogating a member of the opposite sex, advise the individual about the right to request the presence of a person of the same sex. As an alternative, a CI agent of the same sex could conduct the interview.
c. In any event, the CI agent should ensure that a third person is present, or within constant hearing distance, during any interview of a member of the opposite sex. This person must possess the necessary security clearance for the subject matter to be discussed.
d. Should questions arise during the interview that could prove embarrassing, the CI agent, before asking such questions, should advise the individual being questioned that such questions will be asked.
e. The CI agent may have another person present during such interviews, even though the Source or SUBJECT does not make a request. If the individual being questioned objects to the presence of another individual and would be less cooperative in another person's presence, have that objection and its basis reduced to writing and signed by the Source or SUBJECT, and then have the other person in attendence withdraw. If the objection is merely to the visual presence of the third party and not to the third party listening to the statement, make provisions to have the other person in attendence within normal voice range of the place of questioning, but out of sight.
f. In those investigations where the member of the opposite sex has a recent history of serious mental or nervous disorders, another member of the opposite sex must be present during the interview.
Section II
INVESTIGATIVE LEGAL PRINCIPLES
COUNTER-HUMAN INTELLIGENCE TECHNIQUES AND PROCEDURES
A-II-1. General.
This section looks at the legal basis for CI activities. It begins with a short discussion of the EO and the implementing of DOD and Army regulations covering intelligence activities. Section II provides strict guidelines and procedures requiring a thorough knowledge of criminal law, methods of obtaining and processing evidence, an individual's rights, and regulation oversight. It lays the ground work for the investigative and reporting sections to follow.
a. AR 381-10 sets policies and procedures governing the conduct of intelligence activities by Army intelligence components. It proscribes certain types of activities. AR 381-20 implements EO 12333, proscribing certain types of activities and strictly regulating actions commonly referred to as special collection techniques. Currently, it is the governing regulation applicable to MI assets. Neither regulation is a mission statement nor does it task entities or individuals to collect information. Instead, they constitute rules of engagement for collecting information on US persons.
b. The importance of understanding these regulations and following its guidelines to accomplish the mission cannot be overstressed. It is imperative that the individuals requiring the collection of information read and understand the—
(1) Restrictions placed on collecting information concerning US persons.
(2) Definition of the terms "collection" and "US person."
(3) Retention and dissemination of that information.
(4) Use of special collection techniques.
(5) Process of identifying and reporting questionable activities or activities in violation of these regulations, US law, or the US Constitution.
c. CI agents should seek constant assistance from their local judge advocate on the interpretation and application of the procedural guidelines contained in these regulations. Rely only on a trained lawyer's interpretation when seeking to implement any of the special collection procedures.
d. Because of the nature of this work, CI agents must at least understand the basic legal principles. Decisions made by the CI agent are frequently guided by legal concepts. Only a CI agent who is familiar with governing legal principles is able to conduct these tasks efficiently, and within the parameters of the law.
A-II-2. Criminal Law.
Although the Army agent's criminal investigatory responsibility is limited to crimes involving national security, the CI agent must understand general criminal law as well.
a. A crime almost always requires proof of a physical act, a mental state, and the concurrence of the act and the mental state. Criminal law is not designed to prosecute persons who commit acts without a "guilty" intent. For example, a reflex action by an epileptic would not subject the epileptic to criminal liability. Additionally, criminal law is not directed at punishing individuals who privately plan criminal activity when those plans are not combined with action.
b. The act required for criminal prosecution may be a willful act or an omission to act when so required by law. Espionage, the unauthorized receipt of classified information, is an act punishable as a crime. The failure to report missing classified documents is an example of an omission to act punishable as a crime. The law recognizes several different mental states. National security crimes frequently distinguish between specific and general intent. Specific intent requires that an individual act with one of two mental elements:
(1) Purposely, indicating a desire to cause a particular result.
(2) Knowingly, indicating that the individual is substantially certain that the act will cause the result.
c. General intent is indicated by an individual who commits an act with knowledge that an unjustifiable risk of harm will occur. This definition of general intent, and the example below, are specific to the crime of sabotage (Title 18, US Code, Sections 2151-2156) which contains both specific and general elements, and are not necessarily representative of the notion of general intent as a generic criminal law concept.
Alpha, a service member, places a bolt in the engine of an F-16 aircraft. If Alpha placed the bolt in the engine with the specific intent to harm the national defense by the loss of a combat aircraft, Alpha may be convicted of sabotage. However, if Alpha placed the bolt in the engine because of a dissatisfaction with the service, and not to harm specifically the national defense, he may still be convicted of sabotage. This is true because Alpha acted in a manner indicating that he knew that an unjustifiable risk of harm would result from the act of tampering with the aircraft. Since the loss of the aircraft would hamper the national defense effort, Alpha generally intended to commit sabotage in knowing of the risk to the national defense by the act, and yet, consciously disregarding the risk.
d. The inchoate or incomplete crimes are of particular importance to CI agents. These crimes are conspiracy, attempt to commit a specific crime, and solicitation to commit a crime.
(1) Article 81, United States Manual for Courts-Martial, 1984, identifies the following elements of conspiracy:
(a) That the accused entered into an agreement with one or more persons to commit an offense under the code.
(b) That while the agreement continued to exist, and while the accused remained a party to the agreement, the accused or at least one of the co-conspirators performed an act for the purpose of bringing about the object of the conspiracy. The overt act required for a conspiracy may be legal:
Alpha and Bravo conspire to commit espionage. Bravo rents a post office box in which classified information is to be placed to distribute to a foreign agent. At the time Bravo rents the box and before any classified material has been placed in the box, Alpha and Bravo may be arrested and charged with conspiracy to commit espionage.
(2) Article 80, United States Manual for Courts-Martial, 1984, lists the following elements of attempt:
(a) That the accused did a certain overt act.
(b) That the act was done with the specific intent to commit a certain offense under the code.
(c) That the act amounted to more than mere preparation.
(d) That the act apparently tended to effect the commission of the intended offense:
Alpha intends to commit espionage by receiving classified information from Bravo. Unknown to Alpha, Bravo is actually working for CI. Bravo provides Alpha with blank papers. Alpha is arrested as he picks up the papers. Alpha may be charged with and convicted of attempted espionage.
(3) Article 82, United States Manual for Courts-Martial, 1984, identifies the following elements of solicitation: That the accused solicited or advised a certain person or persons to commit any of the four offenses named in Article 82; and that the accused did so with the intent that the offense actually be committed.
(a) Sedition and mutiny are identified in Article 94, United States Manual for Courts-Martial, 1984, as two of the four offenses that may be solicited. CI agents must, therefore, investigate to determine whether a solicitation to commit an act of sedition or mutiny has occurred.
(b) Solicitation does not require that the substantive crime (sedition) actually be committed. The accused need only advise or encourage another to commit the substantive crime. The remaining two crimes under Article 82 are not of CI interest.
A-II-3. Evidence.
a. The United States Manual for Courts-Martial, 1984, contains the rules of evidence applicable in courts-martial. AR 15-6 governs most administrative proceedings. AR 15-6 limits the admissibility of evidence to it being relevant and material. The CI agent must only ask whether the particular piece of evidence tends to prove or disprove a fact of consequence in the adjudication. If it does, it is admissible in an administrative hearing. The only exception to this rule is if the evidence violates the severely limited exclusionary rules applicable to administrative hearings.
b. A respondent's confession or admission, obtained by unlawful coercion or inducement likely to affect its truthfulness, will not be accepted as evidence against that respondent in an administrative proceeding. The failure to advise a respondent of Article 31, UCMJ, or Fifth Amendment rights does not, by itself, render the confession or admission inadmissible in an administrative hearing. Evidence found as the result of a search, conducted or directed by a member of the armed forces acting in an official capacity who knew the search was illegal, will not be admissible in an administrative hearing.
c. Evidence unlawfully obtained through any of the ways covered in this appendix is generally inadmissible as evidence against the suspect or accused. Any other evidence subsequently obtained or derived as a result of this evidence is likewise inadmissible. Whether the use of a particular item in evidence violates an individual's rights is usually a complex and technical determination. The CI agent should obtain advice from the local SJA specified by the unit in its SOP.
A-II-4. Rights.
The remainder of this section discusses the constitutional rights of a suspect or accused person during an investigation and the legal issues involved when obtaining evidence by means of interviews or interrogations, searches and seizures, and apprehensions. A violation of a person's legal rights will substantially, if not completely, reduce the chances of a successful criminal prosecution.
a. Interviews and interrogations. Article 31, UCMJ, and the Fifth Amendment to the US Constitution prohibit government agents from compelling any person to incriminate oneself or to answer any question, the answer to which may tend to incriminate. One may remain absolutely silent and not answer any questions. To be admissible against a person, a confession or admission must be voluntary. A statement obtained through coercion (or other unlawful inducement) is termed involuntary. Physical violence, confinement, and interrogation to the point of exhaustion are examples of acts which may produce involuntary statements.
(1) Courts will use a "reasonable person" test to determine whether the investigator should have considered the individual a suspect and, therefore, given an advisement of rights under Article 31, UCMJ. If individuals appear confused as to their rights or their status, the CI agent should make every reasonable effort to remove the confusion. As the factors that affect a proper warning may be changed by court decision, the CI agent should seek appropriate advice on a continuing basis from a judge advocate. Under Article 31, UCMJ, anyone subject to the UCMJ who is suspected of a crime and who is interviewed by an agent who is also subject to the UCMJ must be advised of his rights.
(2) To enforce the constitutional prohibition against psychologically coerced confessions, Congress, the Supreme Court, and the Court of Criminal Appeals (formerly Court of Military Appeals) have acted to require government agents to advise all suspects and accused persons of their legal rights before questioning. Failure to give the advisement, even to a suspect who is a lawyer or CI agent, will result in the exclusion of the interviewee's statements at trial. Therefore, before beginning suspect interviews, the CI agent informs the individual of his official position, the fact that the individual is a suspect or accused, and the nature of the offense of which he is accused or suspected. If unsure of the precise charge, the CI agent will explain, as specifically as possible, the nature of the facts and circumstances which have resulted in the individual's being considered a suspect.
(3) If a suspect waives the Article 31, UCMJ, rights, the government must be prepared at trial to prove that the defendant understood the rights and chose to waive them voluntarily, knowingly, and intelligently. This is a greater burden than merely showing that the suspect was read the rights and did not attempt to assert or invoke them. Whether the government can sustain this burden at trial depends largely on the testimony and written record furnished by the CI agent who conducted the interview.
(4) The explanation of rights set forth below replaces all previous explanations of legal rights, including the customary reading of Article 31, UCMJ, and the Fifth Amendment to the US Constitution. A mere recitation of this advisement, however, does not assure that subsequent statements by the suspect will be admissible in court, as it must be shown that the suspect, in fact, understood the rights.
(5) The explanation of rights will not suffice if delivered in an offhand or ambiguous manner. The tone of the interrogator's voice should not suggest that the advisement is a meaningless formality. It also would be improper for the interrogator to play down the seriousness of the investigation or play up the benefits of cooperating. In short, the interrogator must not, by words, actions, or tone of voice, attempt to induce the individual to waive the right to remain silent or the right to counsel. Such action will be denounced by the courts as contrary to the purpose of the explanation of rights requirement.
(6) The same result will occur if the interrogator accidentally misstates or confuses the provisions of the advisement. In addition, all other evidence offered will become suspect, for besides excluding illegally obtained statements, the court may reject—and administrative boards are free to reject—any evidence which is not the logical product of legally obtained statements.
(7) Tricking, deceiving, or emphasizing the benefits of cooperating with the government have not been declared illegal per se. The methods used must merely be directed toward obtaining a voluntary and trustworthy statement and not toward corrupting an otherwise proper Article 31, UCMJ, and the Fifth Amendment rights advisement. The CI agent administers the advisement of rights, in accordance with DA Form 3881. When the suspect appears confused or in doubt, the interrogator should give any further explanations by way of a readvisement of the rights.
(8) If the interviewee indicates a desire to consult with counsel for any reason, the interrogator should make no further attempt to continue the questioning until the suspect has conferred with counsel or has been afforded the opportunity to do so. The interrogator may not subsequently continue the questioning unless the interviewee's counsel is present (or unless the interviewee voluntarily initiates further contact with the interrogator. If suspects decide to waive any right, such as the right to have counsel present at the interrogation or the right to remain silent, the interrogator will inform them that they may reassert their rights at any time.
(9) Under no circumstances will the suspect be questioned until the interrogator is satisfied that the individual understands the rights. The interrogator will ask the suspect to sign a waiver certificate (Part 1, DA Form 3881).
(10) If a military member, subject to the code, is suspected of an offense under the UCMJ, the person is entitled to be represented by an attorney at government expense. This can be a military lawyer of the member's choice or, if the requested lawyer is not reasonably available, a detailed military lawyer from the local Trial Defense Service Office. The suspect may also retain a civilian lawyer at no expense to the government. If an appointed counsel is refused, the suspect must have a reasonable basis for that refusal, for example, obvious incompetency. However, the suspect may not arbitrarily declare the counsel unacceptable.
(11) If the suspect requests a specific civilian lawyer, the interrogator must permit the suspect to retain one, and must not continue the interrogation unless the suspect's lawyer is present when questioning resumes, or the suspect voluntarily initiates the resumption of questioning and declines the presence of counsel. The interrogator should assist the individual in obtaining acceptable counsel. The interrogator may not limit the suspect to one telephone call or otherwise interfere in the assertion of the right to counsel.
(12) Civilians generally are not entitled to have counsel provided for them by the armed services. If a civilian suspect demands an attorney, the interrogator must permit the suspect to retain counsel. If the suspect has no lawyer, the interrogator should aid in obtaining legal counsel by providing the suspect with the names and addresses of local agencies that provide legal services.
(13) Such organizations as Legal Aid and the Lawyer's Referral Service are generally listed in local telephone directories. It is to the interrogator's advantage to aid the suspect, since the interrogator may initiate further interrogation only when the suspect is properly represented and counsel is present at the subsequent interrogation. The interrogator should direct all questions about legal representation to the local SJA.
(14) The interrogator should be prepared to question the SUBJECT about each right. Whenever possible, the interrogator should make a verbatim recording of these questions and answers. If this is not possible, the interrogator should ask the SUBJECT to acknowledge both the advisement of rights and an understanding of each right in writing.
(15) It is highly desirable to obtain oral and written acknowledgments. With evidence of both oral and written acknowledgments, the interrogator is well prepared to rebut any charge that the SUBJECT did not understand the rights.
(16) The interrogator should obtain evidence in writing that the SUBJECT made a conscious and knowledgeable decision to answer questions without a lawyer (or to speak with the assistance of a lawyer). See Figure A-II-1 for questions to ask a SUBJECT to assure an understanding of rights.
- Do you understand that you have the right to have a lawyer of your choice during this interview to advise and assist you?
- Do you also understand that your right to a military counsel means a professional lawyer and not just an officer or military superior? (Military only)
- Do you understand that the Army will provide you with a military lawyer free of charge?
- Do you understand that if you decide to answer questions that you may stop whenever you choose?
- Do you understand that anything you say will be made a matter of written record and can be used against you in a court of law?
Figure A-II-1. Questions to ask a SUBJECT to assure an understanding of the rights.
(17) If, at any time and for any reason, the SUBJECT indicates in any manner a reluctance to answer any more questions or wants to see a lawyer, the interrogator must stop immediately. The interrogator should make no attempt to persuade the SUBJECT to change his or her mind. If the SUBJECT does not want to stop the interrogation entirely, but chooses to refuse to answer some questions while answering others, the interrogator is under no obligation to continue but should certainly do so in most cases.
(18) However, the interrogator must not end the interrogation in a manner calculated to intimidate, induce, or trick the SUBJECT into answering questions that the SUBJECT does not care to answer. Under no circumstances should the interrogator ask the SUBJECT why he or she decided to reassert the rights.
(19) Article 31, UCMJ, also prohibits any use of coercion, unlawful influence, or unlawful inducement in obtaining any other evidence from a SUBJECT or accused. One general rule is that SUBJECTs may not be compelled to provide incriminating evidence against themselves through the exercise of their own mental faculties, as for example by making an oral or written statement. Conversely, a SUBJECT may be compelled to provide evidence if the form of evidence will not be affected by conscious thought, and provided the means of coercion (or compelled production) fall within the limits of fundamental decency and fairness. As examples, Article 31, UCMJ, does not prohibit the taking of the following nontestimonial evidence from SUBJECTs: fingerprints, blood samples, and handwriting or voice exemplars. These rules are often quite difficult to apply unless guidance is obtained from a legal officer or judge advocate.
(20) If a SUBJECT has been interrogated without a proper rights advisement, it is possible to correct the defect and proceed after a valid advisement of rights. If the CI agent does not know whether a prior statement was properly obtained, or does know that an impropriety occurred, the agent should provide an additional, accurate advisal of rights, and advise the SUBJECT that any statements given pursuant to defective procedures will not be admissible. This technique will minimize or eliminate the taint of the earlier errors and increase the likelihood of admissibility for the subsequent statement. (Rule 304, Manual for Courts-Martial, 1984.)
b. Search and seizure. The Fourth Amendment of the US Constitution, the Manual for Courts-Martial, and AR 381-10, Procedure 7, protect individuals against unreasonable searches and seizures of their persons, houses, papers, and effects and advises that this right will not be violated. The Fourth Amendment applies in our federal, state, and military court systems.
(1) An unlawful search is one made of a person, a person's house, papers, or effects without probable cause to believe that thereon or therein are located certain objects which are subject to lawful seizure. Probable cause to search exists when there is a reasonable belief that the person, property, or evidence sought is located in the place or on the person to be searched. It means more than "mere suspicion" or "good reason to suspect"( based, for example, on a preliminary or unsubstantiated report), but may be based on hearsay or other legally obtained information. The existence of probable cause to search permits an investigator to seek and obtain a search warrant or authorization from an appropriate judicial or military authority and conduct the desired search. The existence of probable cause may also justify an immediate search without a warrant if exigent circumstances (for example, hot pursuit into a residence, or investigation centering around an operable, movable vehicle) give rise to a reasonable belief that a delay to obtain a warrant would result in removal or destruction of the evidence.
(2) Generally, evidence found as a result of an illegal search or seizure is inadmissible in a military trial and might well taint other evidence, thus precluding further judicial action if a timely motion is made to suppress. Seek advice from the local SJA on exceptions to this rule. The legality of each search necessarily depends on all of the facts in each situation. A search may be overt or covert. The following are types of legal searches:
(a) A search conducted in accordance with the authority granted by proper search warrant is lawful. The warrant must be issued from a court or magistrate having jurisdiction over the place searched. On the installation, this may be a military judge or magistrate. Military judges and magistrates may issue search authorizations based upon probable cause pursuant to Military Rule of Evidence 315(d) and AR 27-10.
(b) A search of an individual's person, the clothing worn, and of the property in immediate possession or custody is lawful when conducted as incident to the lawful apprehension of such person.
(c) A search is lawful when made under circumstances requiring immediate action to prevent the removal or disposal of property believed on reasonable grounds to be evidence of a crime. (d) A search is legal when made with the freely given consent of the owner in possession of the property searched. However, such consent must be the result of a knowing and willing waiver of the rights of the individual concerned and not the mere peaceful submission to apparent lawful authority. Circumstances may dictate the need to obtain written permission of the owner to avoid later denials that permission was freely given.
(e) A commanding officer having jurisdiction over property owned or controlled by the US and under the control of an armed force may lawfully authorize the search of such property. It is immaterial whether or not the property is located in the US or a foreign country. Such a search must also be based on probable cause.
(3) For most purposes, routine physical security inspections in accordance with AR 380-5, and routine investigations of military or civilian personnel when entering or leaving military areas are not considered to be searches but are treated as legitimate administrative inspections or inventories. Contraband may be seized any time.
(4) If possible, the CI agent should request, in writing, the authority to search and should state sufficient factual information to support a conclusion that an offense has occurred or will occur and evidence of the offense is located at the place sought to be searched. Permission to search should be granted by endorsement to such a request. The law of search and seizure must always be related to the actual circumstances; the advice of an SJA or legal officer should be obtained in any doubtful case. The following procedures, however, are valid for any search:
(a) The CI agent secures all available evidence that an offense has been committed and that property relating to the offense is located at a specific place.
(b) The CI agent submits this evidence to the person with authority to order a search of the place or property.
(c) If the place or property is located in a civilian community in the US, the evidence is submitted to the judge or court with authority to issue a search warrant. To obtain a search warrant from a civilian court, CI agents must establish liaison with local civilian police agencies that are authorized to request search warrants and perform the search. The supporting SJA frequently performs a military-civilian liaison function, and should be consulted when such warrants are desired.
(d) If the place or property is located in a foreign country or occupied territory and is owned, used, or occupied by persons subject to military law or to the law of war, the evidence is submitted to a commanding officer of the US Forces who has jurisdiction over personnel subject to military law or to the law of war.
(e) If the place where the property is owned or controlled by the US is under the control of an armed force wherever located, the evidence is submitted to the commanding officer having jurisdiction over the place where the property is located.
(f) The person with authority to order a search must find in the evidence probable cause to believe that the specified place or property contains specific objects subject to lawful seizure.
(g) If the person finds probable cause, that person may then lawfully authorize the search.
(h) Having been authorized, the CI agent may search the specified place or property for the specified objects.
(5) It is possible to have a legal seizure during an illegal search. (For example, the seizure of contraband is always legal, although the illegality of the search may prevent the use of such contraband as evidence.) It is possible to have an illegal seizure during a legal search. In any given judicial procedure, the first point of inquiry will be the legality of the search. If it was illegal, there will be no need to go any further; only if the search was legal will it become necessary to determine the legality of the seizure.
(6) If the search is lawful, certain objects may be seized and admitted in evidence against the suspect:
(a) Contraband, such as property which is prohibited by law. Examples are drugs and untaxed liquor.
(b) Fruits of the crime. Property which has been wrongfully taken or possessed.
(c) Tools or means by which the crime was committed.
(d) Evidence of the crime, such as clothing.
c. Apprehension. Apprehension (called "arrest" in many civilian jurisdictions) is the taking of a person into custody. A person has been taken into custody or apprehended when his or her freedom of movement is restricted in any substantial way.
(1) Authorized individuals may apprehend persons subject to the UCMJ upon reasonable belief that an offense has been committed and that the person to be apprehended committed the offense. This is sufficient probable cause for an apprehension. The authority of the CI agent to apprehend is specified in the following documents: Article 7, UCMJ; Rule 302, Manual for Courts-Martial, 1984; and AR 381-20.
(2) The basis for arrest by civilian police depends on the particular jurisdiction concerned. In general, civilian police make arrests either—
(a) By a warrant upon a showing of probable cause to a magistrate.
(b) Without a warrant, but for probable cause, when a felony or misdemeanor is committed or attempted in their presence.
(c) If a reasonable belief exists that the person committed the offense.
(3) Incident to a lawful apprehension, the SUBJECT's person, clothing that is worn, and property in the immediate possession or control may be searched. Any weapon or means of escape may be lawfully seized.
d. Legal restrictions. For legal restrictions, see AR 381-10. For additional explanation and analysis see INSCOM Pamphlet 27-1. For explanations on proper handling of evidence, see AR 195-5 and FM 19-20. Questions should be referred to the serving SJA or legal advisor.
A-II-5. Intelligence Oversight.
a. AR 381-10 mandates that MI personnel conform to the spirit of the regulation in the conduct of intelligence collection. AR 381-10, Procedure 14, concisely states:
Employees shall conduct intelligence activities only pursuant to, and in accordance with, EO 12333 and this regulation. In conducting such activities, employees shall not exceed the authorities granted the employing DOD intelligence components by law; EO, including EO 12333, and the applicable DOD and Army directives.
b. Because of this requirement, intelligence personnel have the responsibility to understand the limits of the authority under which they conduct an activity, and the procedures from the regulation that apply to the given activity.
c. AR 381-10, Procedure 15, obligates each person to report any questionable intelligence activity by electrical message through command channels to HQDA (SAIG-IO). The term "questionable activity" refers to any conduct that constitutes or is related to an intelligence activity that may violate the law, any EO, or any DOD or Army policy including AR 381-10.
Section III
TECHNICAL INVESTIGATIVE TECHNIQUES
TO
Appendix A
COUNTER-HUMAN INTELLIGENCE TECHNIQUES AND PROCEDURES
A-III-1. General.
The conduct of investigations is enhanced many times by emerging sophisticated procedures designed to simplify and shorten the time required to complete certain investigative tasks while ensuring that all evidence, no matter how seemingly insignificant, is thoroughly evaluated. CI units have available to them from higher supporting echelons and from within their own resources, personnel skilled in technical investigative techniques.
a. Technical investigative techniques can contribute materially to the overall investigation. Section III identifies how each technique contributes to the total CI effort. They can assist in supplying the commander with factual information on which to base decisions concerning the security of the command. Investigators can use these techniques in connection with CI and personnel security investigations for LAAs. CI investigators selectively use the following technical services:
- Electronic surveillance.
- Investigative photography.
- Laboratory analysis.
- Polygraph (authorized for use in local access investigations).
- TEMPEST.
- Computer CE capabilities.
b. In addition, specially trained CI agents conduct TSCM investigations to detect clandestine surveillance systems. TSCM personnel and intelligence polygraph examiners are also trained and experienced CI agents.
A-III-2. Electronic Surveillance.
Electronic surveillance is the use of electronic devices to monitor conversations, activities, sound, or electronic impulses. It is an aid in conducting investigative activities. The US Constitution; EO 12333; and AR 381-10, AR 381-14 (S), and AR 381-20 regulate the use of wiretapping and electronic eavesdropping.
a. Technical surveillance methodology, including those employed by FIS, consists of—
(1) Pickup devices. A typical system involves a transducer (such as a microphone, video camera, or similar device) to pick up sound or video images and convert them to electrical impulses. Pickup devices are available in practically any size and form. They may appear to be common items, such as fountain pens, tie clasps, wristwatches, or household or office fixtures. It is important to note that the target area does not have to be physically entered to install a pickup device. The availability of a power supply is the major limitation of pickup devices. If the device can be installed so its electrical power is drawn from the available power within the target area, there will be minimal, if any, need for someone to service the device.
(2) Transmission links. Conductors carry the impulses created by the pickup device to the listening post. In lieu of conductors, the impulses can go to a transmitter which converts the electrical impulses into a modulated radio frequency (RF) signal for transmission to the listening post. The simplest transmission system is conventional wire. Existing conductors, such as used and unused telephone and electrical wire or ungrounded electrical conduits, may also be used. The development of miniature electronic components permits the creation of very small, easily concealed RF transmitters. Such transmitters may operate from standard power sources or may be battery operated. The devices themselves may be continuously operated or remotely activated.
(3) Listening posts. A listening post consists of an area containing the necessary equipment to receive the signals from the transmission link and process them for monitoring or recording.
(a) Listening posts use a receiver to detect the signal from an RF transmission link. The receiver converts the signal to an audio-video frequency and feeds it to the monitoring equipment. Use any radio receiver compatible with the transmitter. Receivers are small enough to be carried in pockets and may be battery operated.
(b) For wire transmission links only, a tape recorder is required. You can use many commercially available recorders in technical surveillance systems. Some of these have such features as a voice actuated start-stop and variable tape speeds (extended play). They may also have automatic volume control and can be turned on or off from a remote location.
b. Monitoring telephone conversations is one of the most productive means of surreptitious collection of information. Because a telephone is used so frequently, people tend to forget that it poses a significant security threat. Almost all telephones are susceptible to "bugging" and "tapping."
(1) A bug is a small hidden microphone or other device used to permit monitoring of a conversation. It also allows listening to conversations in the vicinity of the telephone, even when the telephone is not in use.
(2) A telephone tap is usually a direct connection to the telephone line which permits both sides of a telephone conversation to be monitored. Tapping can be done at any point along the line, for example, at connector blocks, junction boxes, or the multiwire cables leading to a telephone exchange or dial central office. Telephone lineman's test sets and miniature telephone monitoring devices are examples of taps. Indirect tapping of a line, requiring no physical connection to the line, may also be accomplished.
(3) The most thorough check is not absolute insurance against telephone monitoring. A dial central office or telephone exchange services all telephone lines. The circuits contained within the dial central office allow for the undetected monitoring of telephone communications. Most telephone circuits servicing interstate communications depend on microwave links. Communications via microwave links are vulnerable to intercept and intelligence exploitation.
c. Current electronic technology produces technical surveillance devices that are extremely compact, highly sophisticated, and very effective. Miniaturized technical surveillance systems are available. They can be disguised, concealed, and used by a FIS in a covert or clandestine manner. The variations of their use are limited only by the ingenuity of the technician. Equipment used in technical surveillance systems varies in size, physical appearance, and capacity. Many are identical to, and interchangeable with, components of commercially available telephones, calculators, and other electronic equipment.
A-III-3. Investigative Photography and Video Recording.
a. Photography and video recording in CI investigations includes—
- Identification of individuals. CI agents perform both overt and surreptitious photography and video recording.
- Recording of incident scenes. Agents photograph overall views and specific shots of items at the incident scene.
- Recording activities of suspects. Agents use photography and video recording to provide a record of a suspect's activities observed during surveillance or cover operations.
b. A photograph or video recording may be valuable as evidence since it presents facts in pictorial form and creates realistic mental impressions. It may present evidence more accurately than a verbal description. Photographs permit consideration of evidence which, because of size, bulk, weight, or condition, cannot be brought into the courtroom.
c. To qualify as evidence, photographs and video recordings must be relevant to the case and be free of distortion. A person who is personally acquainted with the locale, object, person, or thing represented must verify the photograph or video recording. This is usually the photographer. The agent will support photographs and video recordings used as evidence by notes made at the time of the photography These notes provide a description of what the photograph includes. The notes will contain—
- The case number, name of the subject, and the time and date that the photographs or video recordings were taken.
- Technical data, such as lighting and weather conditions and type of film, lens, and camera used.
- Specific references to important objects in the photograph.
d. These notes may be retained on a form such as a photo data card shown in Figure A-III-1.
e. Agents can obtain specialized photographic development support from the Intelligence Materiel Activity, Fort Meade, MD. f Physical surveillance of US persons including photography and video recording, is governed by AR 381-10, Procedure 9.
A-III-4. Laboratory analysis.
We must anticipate the use of false documentation and secret writing by foreign intelligence agents in many CI investigations. Detection requires specially trained personnel and laboratory facilities. The CI unit SOP should list how this support is obtained.
A-III-5. Polygraph.
a. The polygraph examination is a highly structured technique conducted by specially trained CI technicians and civilians certified by proper authority as polygraph examiners. Provisions of AR 195-6 cover the polygraph program generally; AR 381-20 covers intelligence polygraphs.
(1) AR 195-6 describes general applicability, responsibilities, and use of polygraph; records processing; and selection and training of DA polygraph examiners.
(2) AR 381-20 authorizes intelligence polygraphs for CI investigations, foreign intelligence and CI operations, personnel security investigations, access to SCI, exculpation in CI and personnel security investigations; and CI scope polygraph (CSP) examinations in support of certain programs or activities listed in AR 381-20.
b. The conduct of the polygraph examination is appropriate, with respect to investigations, only when—
(1) All investigative leads and techniques have been completed as thoroughly as circumstances permit.
(2) The subject of the investigation has been interviewed or thoroughly debriefed.
(3) Verification of the information by means of polygraph is deemed essential for completion or continuation of the investigation.
c. Do not conduct a polygraph examination as a substitute for securing evidence through skillful investigation and interrogation. The polygraph examination is an investigative aid and can be used to determine questions of fact, past or present. CI agents cannot make a determination concerning an individual's intentions or motivations, since these are states of mind, not fact. However, consider the examination results along with all other pertinent information available. Polygraph results will not be the sole basis of any final adjudication.
d. Conduct polygraph examinations during CI and personnel security investigations to—
- Determine if a person is attempting deception concerning issues involved in an investigation.
- Obtain additional leads concerning the facts of an offense, the location of items, whereabouts of persons, or involvement of other, previously unknown individuals.
- Compare conflicting statements.
- Verify statements from witnesses or subjects to include CI and personnel security investigations.
- Provide a just and equitable resolution of a CI or personnel security investigation when the subject of such an investigation requests an exculpatory polygraph in writing.
e. Conduct intelligence polygraph examinations to—
- Determine the suitability, reliability, or creditability of agents, sources, or operatives of foreign intelligence or CI operations.
- Determine the initial and continued eligibility of individuals for access to programs and activities authorized CSP examination support.
f. The polygraph examination consists of three basic phases: pretest, intest, and posttest.
- During the pretest, appropriate rights advisement are given and a written consent to undergo polygraph examination is obtained from all examinees who are suspects or accused. Advise the examinee of the Privacy Act of 1974 and the voluntary nature of examination. Conduct a detailed discussion of the issues for testing and complete the final formulation of questions to be used during testing.
- During the intest phase, ask previously formulated and reviewed test questions and monitor and record the examinee's responses by the polygraph instrument. Relevant questions asked during any polygraph examination must deal only with factual situations and be as simple and direct as possible. Formulate these questions so that the examinee can answer only with a yes or no. Never use or ask unreviewed questions during the test.
- If responses indicate deception, or unclear responses are noted during the test, conduct a posttest discussion with the examinee in an attempt to elicit information from the examinee to explain such responses.
g. A polygraph examiner may render one or more of four possible opinions concerning the polygraph examination.
- No opinion (NO) is rendered when less than two charts are conducted concerning the relevant issues, or a medical reason halts the examination. Normally, three charts are conducted.
- Inconclusive (INCL) is rendered when there is insufficient information upon which to make a determination.
- No deception indicated (NDI) is rendered when responses are consistent with an examinee being truthful regarding the relevant areas.
- Deception indicated (DI) when responses are consistent with an examinee being untruthful to the relevant test questions.
h. Certain mental or physical conditions may influence a person's suitability for polygraph examination and affect responses during testing. CI agents should report any information they possess concerning a person's mental or physical condition to the polygraph examiner before scheduling the examination. Typical conditions of concern are—
- Mental disorders of any type.
- Any history of heart, respiratory, circulatory, or nervous disorders.
- Any current medical disorder, to include colds, allergies, or other conditions (such as pregnancy or recent surgery).
- Use of drugs or alcohol before the examination.
- Mental or physical fatigue.
- Pain or physical discomfort.
i. To avoid such conditions as mental or physical fatigue, do not conduct prolonged or intensive interrogation or questioning immediately before a polygraph examination. The CI agent tells the potential examinee to continue taking any prescribed medication and bring it to the examination. Based on information provided by the CI agent and the examiner's own observations, the polygraph examiner decides whether or not a person is fit to undergo examination by polygraph. When the CI agent asks a person to undergo a polygraph examination, the person is told that the examination is voluntary and that no adverse action can be taken based solely on the refusal to undergo examination by polygraph. Further, the person is informed that no information concerning a refusal to take a polygraph examination is recorded in any personnel file or record.
j. The CI agent will make no attempt to explain anything concerning the polygraph instrument or the conduct of the examination. If asked, the CI agent should inform the person that the polygraph examiner will provide a full explanation of the instrument and all procedures before actual testing and that all test questions will be fully reviewed with the potential examinee before testing.
k. Conduct polygraph examinations in a quiet, private location. The room used for the examination must contain, as a minimum, a desk or table, a chair for the examiner, and a comfortable chair with wide arms for the examinee. The room may contain minimal, simple decorations; must have at least one blank wall; and must be located in a quiet, noise-free area. Ideally, the room should be soundproof. Visual or audio monitoring devices may be used during the examination; however, the examiner must inform the examinee that such equipment is being used and whether the examination will be monitored or recorded in any manner.
l. Normally, only the examiner and the examinee are in the room during examination. When the examinee is an accused or suspect female and the examiner is a male, a female witness must be present to monitor the examination. The monitor may be in the examination room or may observe through audio or visual equipment, if such is available.
m. On occasion, the CI agent must arrange for an interpreter to work with the examiner. The interpreter must be fluent in English and the required language, and have a security clearance appropriate to the classification of material or information to be discussed during the examination. The interpreter should be available in sufficient time before the examination to be briefed on the polygraph procedures and to establish the proper working relationship.
n. AR 195-6 describes polygraph reports, records to be maintained, and records distribution. The CI agent must provide the examiner with all files, dossiers, and reports pertaining to the investigation or operation before the examination, and must be available to answer any questions the examiner may have concerning the case.
(1) The CI agent will not prepare any agent reports concerning the results of a polygraph examination. This does not include information derived as a result of pretest or posttest admissions, nor does it include those situations where the CI agent must be called upon by the examiner to question the subject concerning those areas which must be addressed before the completion of the examination.
(2) The polygraph examiner will prepare a DA Form 2802. A copy of this may be provided to the CI agent. Such copies must be destroyed within three months following completion of the investigation or operation. The Investigative Records Repository, Central Security Facility, Fort Meade, MD, maintains the original of the DA Form 2802. Request polygraph support in accordance with INSCOM Pamphlet 381-6.
A-III-6. Technical Surveillance Countermeasures.
a. TSCM versus TEMPEST. TSCM is concerned with all signals leaving a sensitive or secure area, to include audio, video, and digital or computer signals. There is a definite distinction between TSCM and TEMPEST.
(1) TEMPEST is the unintentional emanation of electronic signals outside a particular piece of equipment. Electric typewriters create such signals. The words to focus on in TEMPEST are "known" and "unintentional" emanations. TEMPEST is controlled by careful engineering or shielding.
(2) TSCM is concerned with the intentional effort to gather intelligence by foreign intelligence activities by impulsing covert or clandestine devices into a US facility, or modifying existing equipment within that area. For the most part, intelligence gained through the use of technical surveillance means will be accurate, as people are unaware they are being monitored. At the same time, the implanting of such technical surveillance devices is usually a last resort.
b. Threat. The FIS, their agents, and other persons use all available means to collect sensitive information. One way they do this is by using technical surveillance devices, commonly referred to as "bugs" and "taps." Such devices have been found in US facilities worldwide. Security weaknesses in electronic equipment used in everyday work have also been found worldwide. The FIS easily exploits these weaknesses to collect sensitive or classified conversations as well as the information being processed. They are interested in those things said in (supposed) confidence, since they are likely to reveal future intentions. It should be stressed that the threat is not just audio, but video camera signals, as well as data. Devices are usually placed to make their detection almost impossible without specialized equipment and trained individuals.
c. The TSCM program. The purpose of the TSCM program is to locate and neutralize technical surveillance devices that have been targeted against US Government sensitive or secure areas. The TSCM program is designed to identify and enable the correction of exploitable technical and physical security vulnerabilities. The secondary, and closely interrelated purpose, is to provide commanders and department heads with a comprehensive evaluation of their facilities' technical and physical security postures. The Director of Central Intelligence established the requirement for a comprehensive TSCM program. DODD 5240.5 and AR 381-14 (S) govern the implementation of this program.
(1) The TSCM program includes four separate functions; each with a direct bearing on the program.
(a) Detection. Realizing that the threat is there, the first and foremost function of the TSCM program is to detect these devices. Many times these devices cannot be easily detected. Occasionally, TSCM personnel will discover such a device by accident. When they discover a device, they must neutralize it.
(b) Nullification. Nullification includes both passive and active measures used to neutralize or negate devices that are found. An example of passive nullification is soundproofing. But soundproofing that covers only part of a room is not very helpful. Excessive wires must be removed, as they could be used as a transmission path from the room. Nullification also refers to those steps taken to make the emplacement of technical surveillance systems as difficult as possible. An example of active nullification is the removal of a device from the area.
(c) Isolation. The third function of the TSCM program is isolation. This refers to limiting the number of sensitive or secure areas and ensuring the proper construction of these areas.
(d) Education. Individuals must be aware of the foreign intelligence threat and what part they play should a technical surveillance device be detected. Additionally, people need to be alert to what is going on in and around their area, particularly during construction, renovations, and installation of new equipment.
(2) The TSCM program consists of CI technical investigations and services (such as surveys, inspections, preconstruction advice and assistance) and technical security threat briefings. TSCM investigations and services are highly specialized CI investigations and are not be to confused with compliance-oriented or administrative services conducted to determine a facility's implementation of various security directives.
(a) TSCM survey. This is an all-encompassing investigation. This investigation is a complete electronic, physical, and visual examination to detect clandestine surveillance systems. A by-product of this investigation is the identification of physical and technical security weaknesses which could be exploited by the FIS.
(b) TSCM inspection. Normally, once a TSCM survey has been conducted, it will not be repeated. If TSCM personnel note several technical and physical weaknesses during the survey, they may request and schedule an inspection at a later date. In addition, they will schedule an inspection if there has been an increased threat posed to the facility or if there is some indication that a technical penetration has occurred in the area. DODD 5240.5 specifically states that no facility will qualify automatically for recurrent TSCM support.
(c) TSCM preconstruction assistance. As with other technical areas, it is much less expensive and more effective to build in good security from the initial stages of a new project. Thus, preconstruction assistance is designed to help security and construction personnel with the specific requirements needed to ensure that a building or room will be secure and built to standards. This saves money by precluding costly changes later on.
(3) Army activities request TSCM support in accordance with AR 381-14 (S).
(a) Requests for, or references to, a TSCM investigation will be classified SECRET and marked with the protective marking, NOT RELEASABLE TO FOREIGN NATIONALS. The fact that support is scheduled, in progress, or completed, is classified SECRET.
(b) No request for TSCM support will be accepted via nonsecure means. Nonsecure telephonic discussion of TSCM support is prohibited.
(c) All requests will be considered on a case-by-case basis and should be forwarded through the appropriate major Army command to Commanding General, US Army Intelligence and Security Command, ATTN: IAOPS-CI-TC, Fort Belvoir, VA 22060-5246.
(d) When requesting or receiving support, the facility being inspected must be complete and operational, unless requesting preconstruction advice and assistance. If any additional equipment goes into the secure area after the investigation, the entire area is suspect and the investigation negated.
(e) Fully justified requests of an emergency nature, or for new facilities, may be submitted at any time, but should be submitted at least 30 days before the date the support is required. Unprogrammed requests will be funded by the requestor. Each request for unprogrammed TSCM support must be accompanied by a fund cite to defray the costs of temporary duty (TDY) and per diem.
(4) The compromise of a TSCM investigation or service is a serious security violation with potentially severe impact on national security. Do not compromise the investigation or service by any action which discloses to unauthorized persons that TSCM activity will be, is being, or has been conducted within a specific area. Unnecessary discussion of a TSCM investigation or service, particularly within the subject area, is especially dangerous.
(a) If a listening device is installed in the area, such discussion can alert persons who are conducting the surveillance and permit them to remove or deactivate their devices. When deactivated, such devices are extremely difficult to locate and may require implementation of destructive search techniques.
(b) In the event a TSCM investigation or service is compromised, the TSCM team chief will terminate the investigation or service at once. Report the circumstances surrounding the compromise of the investigation or service to the head of the serviced facility, the appropriate major Army command, and the INSCOM TSCM Program Director. TSCM personnel will not reschedule an investigation or service until the cause and impact of the compromise have been evaluated by the TSCM CI agent, the appropriate agency head, and the INSCOM TSCM Program Director.
(5) When a TSCM survey or inspection is completed, the requestor is usually given reasonable assurance that the surveyed area is free of active technical surveillance devices or hazards.
(a) TSCM personnel inform the requestor about all technical and physical security vulnerabilities with recommended regulatory corrective actions.
(b) The requestor should know that it is impossible to give positive assurance that there are no devices in the surveyed area.
(c) The security afforded by the TSCM investigation will be nullified by the admission to the secured area of unescorted persons who lack the proper security clearance. The TSCM investigation will also be negated by—
- 1 Failing to maintain continuous and effective surveillance and control of the serviced area.
- 2 Allowing repairs or alterations by persons lacking the proper security clearance or not under the supervision of qualified personnel.
- 3 Introducing new furnishings or equipment without a thorough inspection by qualified personnel.
(6) Report immediately the discovery of an actual or suspected technical surveillance device via a secure means, in accordance with guidance provided in AR 381-14 (S). All information concerning the discovery will be handled at a minimum of SECRET. Installation or unit security managers will request an immediate investigation by the supporting CI unit or supporting TSCM element.
Section IV
SCREENING, CORDON, AND SEARCH OPERATIONS
TO
Appendix A
COUNTER-HUMAN INTELLIGENCE TECHNIQUES AND PROCEDURES
A-IV-1. General.
Screening, cordon, and search operations are used to gain intelligence information. Section IV provides the techniques and procedures for these operations. Screening operations identify individuals for further interrogation by CI and interrogators. CI agents may conduct screening at MP roadblocks or checkpoints. Cordon and search operations identify and apprehend persons hostile to our operations. Actual controlling of areas is done by host nation forces assisted by CI, interrogation, and other friendly forces. In some instances, the operation may be exclusively US.
a. In a conventional combat environment, CI screening operations screen refugees, EPW, and civilian internees at mobile and static checkpoints. CI agents normally conduct these operations with other elements such as MP, interrogators, combat troops, CA, and PSYOP teams. These operations require close coordination and planning. The planning may include joint or combined planning. CI exploits cordon and search operations for individuals and information of CI interest, but is not in charge. The commander of the unit performing the cordon and search is in charge.
b. In OOTW, CI agents use cordon and search operations to ferret out the insurgent infrastructure as well as individual unit elements which may use a community or area as cover for their activities or as a support base. CI agents conduct these operations, whenever possible, with host country forces and organizations.
c. Ideally, US Forces, including CI personnel, provide support while host country officials direct the entire operation. Host country personnel should, as a minimum, be part of the screening and sweep elements on any cordon and search operation. In situations where there is no viable host nation government, these operations may be conducted unilaterally or as part of a combined force.
A-IV-2. Counterintelligence Screening.
The purpose of CI screening operations is to identify persons of CI interest or verify persons referred by interrogators who are of CI interest, and gather information of immediate CI interest.
a. Subjects of intelligence interest. Interrogators normally conduct refugee and EPW screening at the EPW compound or refugee screening point. Interrogators refer persons identified for possible CI interest to CI personnel to be screened. CI personnel conduct interrogations with the view to intercepting hostile intelligence agents, saboteurs, and subversives trying to infiltrate friendly lines. As the battle lines in combat change, entire segments of the population may be overrun. The local population in any area may be swelled by refugees and displaced persons (persons from other lands conscripted by enemy forces for labor). The following are examples of categories of persons of CI interest (this list is not all inclusive):
- Persons suspected of attempting to infiltrate through refugee flow.
- Line crossers.
- Deserters from enemy units.
- Persons without identification (ID) papers or forged papers (inconsistent with the norm).
- Repatriated prisoners of war and escapees.
- Members of underground resistance organizations seeking to join friendly forces.
- Collaborators with the enemy.
- Target personalities, such as those on the personalities list (also known as the black, gray, or white lists).
- Volunteer informants.
- Persons who must be questioned because they are under consideration for employment with US Forces or for appointment as civil officials by CA units.
b. Planning and coordination. CI personnel plan these screening operations, as far as possible, in conjunction with the following elements:
- Combat commander. The commander is concerned with channelizing refugees and EPWs through the AO, particularly in the attack, to prevent any hindrance to unit movement, or any adverse effect on unit mission.
- Interrogators. Interrogation personnel must understand what CI is looking for and have the commander's current PIR and information requirements (IR). Close coordination with interrogators is essential for successful CI operations.
- Military police. MP elements are responsible for collecting EPW and civilian internees from capturing units as far forward as possible in the AO. MP units guard the convoys transporting EPW and civilian internees to EPW camps, and command and operate the EPW camps.
- Civil affairs. CA elements, under the G5, are responsible for the proper disposition of refugees.
- Psychological operations. PSYOP elements, under the G3, contribute to screening operations by informing the populace of the need for their displacement.
- Civil authorities in hostile areas. Civil authorities in hostile areas are included in planning only if control has been returned to them.
c. Preparation. Before any screening operation, the CI teams involved should become intimately familiar with all available information or indicators as covered in paragraph A-IV-2f, as well as the following facts:
- Regulations. To have any success, CI personnel must become familiar with all restrictions placed on the civilian population within the enemy-held area, including curfews, travel restrictions, rationing, draft or conscription regulations, civilian labor force mobilization orders, required political organizational membership. Knowledge of these regulations may help the CI screener to detect discrepancies and discern changes in enemy activity.
- Intelligence, infrastructure, organization. In order to identify agents of the enemy intelligence or infrastructure apparatus, CI personnel must be thoroughly familiar with their methods of operation, policies, objectives, offices and suboffices, schools, officials, and known agents. This includes knowing what the enemy calls itself and its organization as well as the known names for the same organization.
- Order of battle. The CI team needs to maintain and have ready access to current OB information. All team members must know what adversary forces they are facing and what units are in the AO. CI teams need to know adversary unit disposition, composition, strength, weaknesses, equipment, their training, history, activities, and personalities. The better CI teams know their adversaries, the better they can employ the principles of CI in support of their own unit's mission.
- Area of operations. CI personnel should also become familiar with the area in which they are operating; particularly geography, landmarks, distances, and travel conditions. Knowing such pertinent information as the political situation, social and economic conditions, customs, and racial problems of the area is essential.
- Lists and information sheets. CI teams should distribute apprehensions lists and information sheets listing indicators of CI interest to the troops, MP, or other personnel assisting with the screening operation. CI teams should make up forms and pass them out to the individuals to be screened requiring them to record personal data. This form will aid in formulating the type of questions to be asked and in determining the informational areas needed to fulfill PIR and IR. Include the following data, plus anything else judged necessary, on the form:
(a) Full name, other names, date and place of birth, current and permanent residences, and current citizenship.
(b) The same information as above concerning the father, mother, and siblings, including the occupation and whereabouts of each.
(c) If married, the names of spouse (including female maiden name), date, place of birth (DPOB), nationality, occupation, and personal data on spouse's family.
(d) The individual's education and knowledge of languages.
(e) Details of the individual's career to include schools, military service, technical and professional qualifications, political affiliations, and countries visited.
(f) Point of departure, destination, and purpose.
NOTE: The Geneva Conventions do not require this, and if the person refuses to give the information, there is nothing that can be done about it. Prepare the form in the native language of the host nation and enemy force, if different. Ensure that it is prepared in the proper dialect of the language.
d. Main battle area screening.
- Capturing troops search EPWs and internees captured in the main battle area (MBA) for weapons and documents, and prepare EPW and civilian internee capture tags. MP tasked with EPW operations collect EPW and civilian internees from capturing units as far forward as possible, normally establishing a division forward EPW and civilian internee collection point in or near the brigade support area (BSA). MP are responsible for subsequent evacuation of EPWs and civilian internees to the division central collection point and further rearward to internment sites.
- Initial screening should take place at the brigade collecting points. The initial screening will, as a minimum, consist of interrogation by intelligence interrogation personnel. Interrogation does not take precedence over rapid evacuation of EPW and civilian internees from dangerous areas. This is required by Article 19, Geneva Convention. Segregate individuals of CI interest from other EPW and civilian internees. Identify them to evacuating MP who will refer them to a CI team at division. EPW and civilian internees of CI interest remain segregated and are referred to CI teams for coordination of more detailed interrogation as they pass through the evacuation process.
- Return those EPW and civilian detainees determined to be of no CI value to normal evacuation channels. Expeditiously transport EPW and civilian internees considered to be of great CI value such as officers of brigade command level or higher or civilian electronics specialists or others of similar background to any desired level of interrogation.
e. Conduct. Because of time and the large numbers of people to be interrogated, it is impossible to interrogate everyone. Civilians moving about the combat area have to be subjected to brief inquiries on a selective basis by MI, CA, PSYOP, and MP personnel. Such brief inquiries are designed to locate and separate suspicious persons from the masses and should be thought of as a preliminary interrogation.
- While some are detained for interrogation, some selected persons are detained for further CI interrogation. Upon notification of a detainee or prisoner of CI interest, a CI team will be dispatched as soon as possible to the collection or screening point. The CI team will then coordinate with the interrogation team to determine the best method for conducting the CI interrogation or screening. If a determination is made that the EPW or detainee is of CI interest, the CI team will either control operational activity or refer the operation to the next higher echelon. If the detainee is to be referred to a higher echelon for the detailed interrogation, furnish a preliminary screening sheet and SPOT report to the evacuating unit. The evacuating unit will deliver the detainee and screening report to the next echelon CI team.
- The CI screening report should include the following:
(a) Identity. Screen all identifying documents in the form of ID cards, ration cards, draft cards, driver's license, auto registration, travel documents, and passport. Record rank, service number, and unit if a person is, or has been a soldier. Check all this information against the form previously filled out by the detainee if this was done.
(b) Background. The use of the form identified earlier will aid in obtaining the information required; however, certain information areas on the forms will have to be clarified, especially if data indicate a suspect category or the person's knowledgeability of intelligence information. If the form has not been filled out at this point, try to gain the information through questioning.
(c) Recent activities. Examine the activities of persons during the days before their detainment or capture. What were they doing to make a living? What connection, if any, have they had with the enemy? Why were they in the area? This line of questioning may bring out particular skills such as those associated with a radio operator, linguist, or photographer. Make physical checks for certain types of calluses, bruises, or stains to corroborate or disprove his story. Sometimes soil on shoes will not match that from the area he claims to come from.
(d) Journey or escape route. CI personnel should determine the route the individual took to get to US lines or checkpoints. Question the individual further on time, distance, and method of travel to determine whether or not the trip was possible during the time stated and with the mode of transportation used. Discrepancies in travel time and distances can be the key to the discovery of an infiltrator with a shallow cover story. By determining what an individual observed enroute, the screener can either check the person's story or pick up intelligence information concerning the enemy forces. Interrogators are well trained in this process and should be called upon for assistance and training.
f. Indicators.
- Use the following indicators in an attempt to identify hostile infiltrators. CI personnel look for persons:
(a) Of military age.
(b) Traveling alone or in pairs.
(c) Without ID.
(d) With unusual documents.
(e) Possessing large amounts of money, precious metals, or gems.
(f) Displaying any peculiar activity.
(g) Trying to avoid detection or questioning.
(h) Using enemy methods of operating.
(i) Having a pro-enemy background.
(j) With a suspicious story.
(k) With a family in enemy areas.
(l) With a technical skill or knowledge.
(m) Who have collaborated.
(n) Who violate regulations in enemy areas. - In addition to interrogation, use the following methods of screening EPWs and refugees:
(a) Apprehension lists.
(b) Low-level informants infiltrated into EPW compounds or camps; civilian internee screens or camps; or refugee screens or centers.
(c) Sound equipment placed in suspect-holding areas or cages.
(d) Polygraph examinations.
(e) Specialized identification equipment, for example, metal-trace detection kits.
g. Checkpoints.
- This type of CI screening requires CI personnel to prepare apprehension lists and indicators to be used by screening teams. Specialized equipment such as metal detection kits would significantly enhance the screening process. These teams will provide the initial screening and will detain and refer suspects to the MI control element for detailed OB or CI interrogation and possible exploitation. Screening teams can be made up of combat troops, MP, CA, intelligence interrogators, and CI agents.
- Place checkpoints shown in Figure A-IV-1 at strategic locations, where there is sufficient space for assembling people under guard and for parking vehicles for search and investigation. Set these up as either mobile or static missions. Post local security to protect the checkpoint and post a sufficient amount of personnel to the front and rear to catch anyone attempting to avoid the checkpoint. The preparation needed for static and mobile checkpoints is identical to other screening operations, and the indicators will remain basically the same.
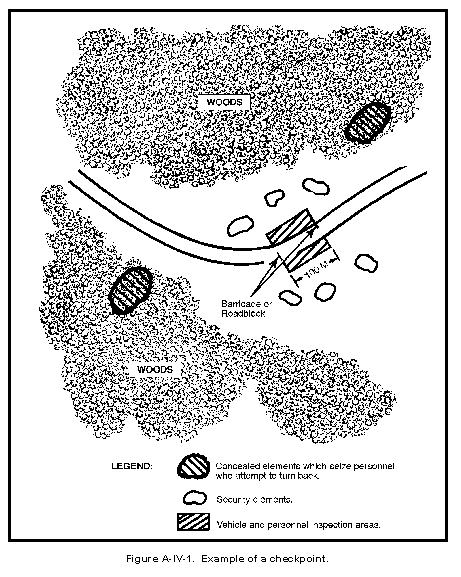
(a) Mobile. Use a mobile checkpoint as a moving system by which the team, either mounted or on foot, briefly selects individuals at random. Locate these checkpoints at various points for periods not to exceed one day.
(b) Static. Static checkpoints are those manned permanently by MP or troops at the entrance to a bridge, town gate, river crossing, or similar strategic point.
A-IV-3. Cordon and Search.
The purpose for conducting cordon and search operations is to identify and apprehend persons hostile to our efforts and to exploit information gathered.
a. Before conducting a community or area cordon and search operation, CI personnel must coordinate with local officials to solicit their support and cooperation. They must coordinate with the host country area coordination center, if established. If not established, they must coordinate with host country intelligence and police organization to—
(1) Obtain their participation in the operation.
(2) Update existing personalities list (black and gray lists).
(3) Arrange to have insurgent defectors, agents, and other knowledgeable personnel present to identify insurgents and their supporters.
(4) Update all intelligence on the community or area.
b. CI personnel must coordinate with appropriate US and host country CA and PSYOP units. Coordination must also be done with the unit conducting the operation. An essential part of preparing for a cordon and search is an update of all intelligence on the community or area.
c. The senior tactical unit commander will be the individual responsible for the conduct of the operation. That commander will plan, with advice from CI, interrogation, CA, and PSYOP personnel, the cordon which is usually deployed at night, and the search which normally begins at first light.
d. Community operations.
(1) The basic operation is the community cordon and search operation shown in Figure A-IV-2. As the screening element sets up the collection or screening station shown in Figure A-IV-3, the sweep element escorts the residents toward the station, leaving behind one resident to care for family belongings, if required by law.
(2) The search element follows behind the sweep element searching houses, storage areas, cemeteries and so forth, with dogs and metal detection equipment. CI personnel are searching for evidence of intelligence collection operations to include communications codes or other such paraphernalia. Each search element should include a CI team with an interrogator team as required, which will have a list of persons of CI interest.
(3) In the collection or screening station, bring the residents to the collection area (or holding area) and then systematically lead them to specific screening stations. Enroute to the screening station, search each individual for weapons. Then lead the residents past the mayor or community leaders (enemy defectors or cooperating prisoners who will be hidden from view so that they can uncompromisingly identify any recognizable enemy). These informants will be provided with the means to notify a nearby guard or a screener if they spot an enemy member. Immediately segregate this individual and interrogate by appropriate personnel.
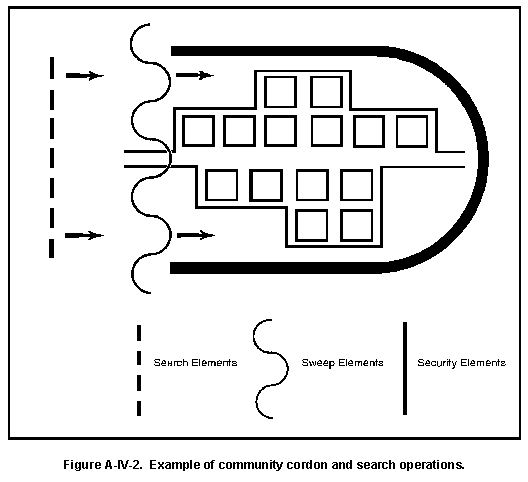
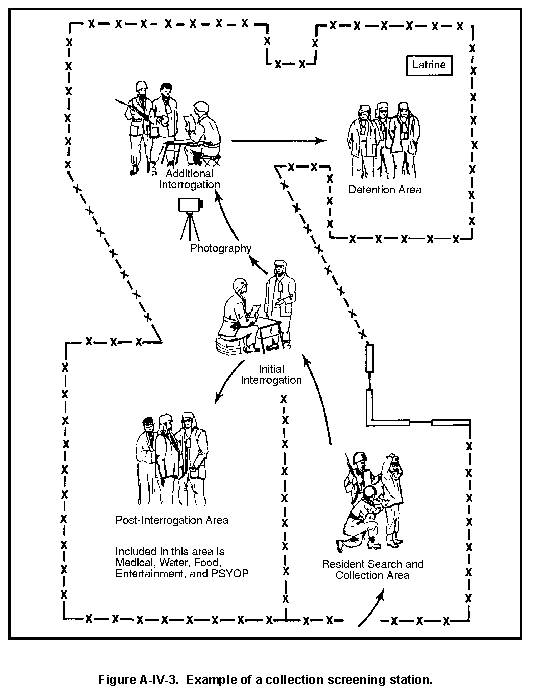
(4) At specific screening stations, ask the residents for identification, check against personalities list (black list), and search for incriminating evidence by electronic equipment.
(5) Move suspected persons on for photographing, further interrogation, or put them in the screening area detention point to be taken back to a base area or area coordination center interrogation facility for detailed interrogation upon completion of the operation.
(6) Pass innocent residents through to the post screening area where they are provided medical assistance and other civic assistance, as well as entertainment and friendly propaganda.
(7) Return any persons caught attempting to escape or break through the cordon immediately to the detention area.
(8) When the operation is terminated, allow all innocent individuals to return to their homes, and remove the enemy suspects under guard for further interrogation. Photograph all members of the community for compilation of a village packet, which will be used in future operations.
e. "Soft" or area operation.
(1) The second type of cordon and search operation is very frequently referred to as the "soft" or area cordon and search. This operation includes the cordoning and searching of a rather vast area (for example, a village area incorporating a number of hamlets, boroughs, town, or villages which are subdivisions of a political area beneath country level).
(2) This type of operation requires a multibattalion military force to cordon off the area; a pooling of all paramilitary, police, CA, and intelligence resources to conduct search and screening; and a formidable logistical backup. This kind of operation extends over a period of days and may take as long as a week or possibly longer.
(3) While screening and search teams systematically go from community to community and screen all residents, military forces sweep the area outside the communities over and over again to seek out anyone avoiding screening. As each resident is screened, CI agents will issue documents testifying to the fact that he was screened and if necessary, allow him restricted travel within the area.
(4) Other population and resources control measures are used as well. Such an opportunity may allow the chance to issue new ID cards and photograph all of the area's residents.
(5) As each community screening proceeds, send individuals who were designated for further interrogation to a centralized interrogation center in the cordoned area. Here, CI personnel will work with intelligence interrogation personnel, both US and indigenous, police, and other security service interrogators.
(6) Besides field files and other expedient facilities, a quick reaction force is located at the interrogation center to react immediately to intelligence developed during the interrogations and from informants planted among the detainees.
Section V
PERSONALITIES, ORGANIZATIONS, AND INSTALLATIONS LIST
TO
Appendix A
COUNTER-HUMAN INTELLIGENCE TECHNIQUES AND PROCEDURES
A-V-1. General.
The effectiveness of CI operations depends largely on the planning that precedes the operation. Early in the planning process the CI officer on the G2 staff directs the efforts to obtain information on the adversary's intelligence, sabotage, terrorism, and subversion capabilities. Collected information is processed and analyzed, and from it the CI officer formulates a list of CI targets. Section V identifies the criteria for the personalities, organizations, and installations list. CI targets are personalities, organizations, and installations of intelligence or CI interest which must be seized, exploited, or protected.
A-V-2. Personalities.
These are persons who are a threat to security, whose intentions are unknown, or who can assist the intelligence and CI efforts of the command. Personalities are grouped into these three categories. For ease in identification, a color code indicates the category. Colors currently in use are black, gray, and white and pertain to the three categories in the order listed above.
a. Black list. The black list is an official CI listing of actual or potential enemy collaborators, sympathizers, intelligence suspects, and other persons whose presence menaces the security of the friendly forces. (Joint Pub 1-02) Black list includes—
- Known or suspected enemy or hostile espionage agents, saboteurs, terrorists, political figures, and subversive individuals.
- Known or suspected leaders and members of hostile paramilitary, partisan, or guerrilla groups.
- Political leaders known or suspected to be hostile to the military and political objectives of the US or an allied nation.
- Known or suspected officials of enemy governments whose presence in the theater of operations poses a security threat to the US Forces.
- Known or suspected enemy collaborators and sympathizers whose presence in the theater of operations poses a security threat to the US Forces.
- Known enemy military or civilian personnel who have engaged in intelligence, CI, security, police, or political indoctrination activities among troops or civilians.
- Other personalities indicated by the G2 as automatic arrestees. Included in this category may be local political personalities, police chiefs, and heads of significant municipal and national departments or agencies, and tribal or clan leaders.
b. Gray list. The gray list contains the identities and locations of those personalities whose inclinations and attitudes toward the political and military objective to the US are obscure. Regardless of their political inclinations or attitudes, personalities may be listed on gray lists when they are known to possess information or particular skills required by US Forces. These people are the "unknowns." They may be individuals whose political motivations require further exploration before they can be used effectively by US Forces. Examples of individuals who may be included in this category are—
- Potential or actual defectors from the hostile cause whose bona fides have not been established.
- Individuals who have resisted, or are believed to have resisted, the enemy government and who may be willing to cooperate with US Forces, but whose bona fides have not been established.
- Scientists and technicians suspected of having been engaged against their will in enemy research projects of high technology programs.
c. White list. The white list contains the identities and locations of individuals who have been identified as being of intelligence or CI interest and are expected to be able to provide information or assistance in existing or new intelligence AIs. They are usually in accordance with, or favorably inclined toward, US policies. Their contributions are based on a voluntary and cooperative attitude. Decisions to place individuals on the white list may be affected by the combat situation, critical need for specialists in scientific fields, and such theater intelligence needs as may be indicated from time to time. Examples of individuals who may be included in this category are—
- Former political leaders of a hostile state who were deposed by the hostile political leaders.
- Intelligence agents employed by US or allied intelligence agencies.
- Key civilians in areas of scientific research, who may include faculty members of universities and staffs of industrial or national research facilities, whose bona fides have been established.
- Leaders of religious groups and other humanitarian groups.
- Other persons who can materially and significantly aid the political, scientific, and military objectives of the US and whose bona fides have been established.
A-V-3. Installations.
Installations on the CI targets list are any building, office, or field position that may contain information or material of CI interest or which may pose a threat to the security of the command. Installations of CI interest include—
a. Those that are or were occupied by enemy espionage, sabotage, or subversive agencies or police organizations, including prisons and detention centers.
b. Those occupied by enemy intelligence, CI, security, or paramilitary organizations including operational bases, schools, and training sites.
c. Enemy communication media and signal centers.
d. Nuclear research centers and chemical laboratories.
e. Enemy political administrative HQ.
f. Public utilities and other installations to be taken under early control to prevent sabotage.
g. Production facilities, supply areas, and other installations to be taken under control to prevent support to hostile guerrilla and partisan elements.
h. Embassies and consulates of hostile governments.
A-V-4. Organizations.
Any group that is a potential threat to the security of the friendly force must be neutralized, rendered ineffective. Groups or organizations which are of concern to CI during tactical operations include—
a. Hostile intelligence, sabotage, subversive, and insurgent organizations.
b. National and local political parties or groups known to have aims, beliefs, or ideologies contrary or in opposition to those of the US.
c. Paramilitary organizations, including students, police, military veterans, and excombatant groups known to be hostile to the US.
d. Hostile sponsored organizations or groups whose objectives are to create dissention and spread unrest among the civilian population in the AO.
A-V-5. Control Measures.
The CI officer and the G2 need a positive way to keep track of the status of CI targets. Called a target reduction plan, it's a checklist used to ensure targets are seized, exploited, or controlled in a timely manner. The plan is keyed to the scheme of maneuver and lists targets as they are expected to appear. When more targets appear than can be exploited, a priority list is used to denote which target takes priority.
a. Priority one targets represent the greatest threat to the command. They possess the greatest potential source of information or material of intelligence or CI value. Priority one targets must be exploited or neutralized first.
b. Priority two targets are of lesser significance than priority one. They are taken under control after priority one targets have been exploited or neutralized.
c. Priority three targets are of lesser significance than priority one or two. They are to be exploited or neutralized as time and personnel permit.
Section VI
COUNTER-HUMAN INTELLIGENCE ANALYSIS
TO
Appendix A
COUNTER-HUMAN INTELLIGENCE TECHNIQUES AND PROCEDURES
A-VI-1. General.
C-HUMINT analysis increases in importance with each new US involvement in worldwide operations. Especially in OOTW, C-HUMINT analysis is rapidly becoming a cornerstone upon which commanders base their concepts operations. This section presents information for analysts to develop some of those products that can enhance the probability of successful operations.
a. MDCI analysts, interrogators, and CI agents maintain the C-HUMINT database. Using this database, they produce—
- Time event charts.
- Association matrices.
- Activities matrices.
- Link diagrams.
- HUMINT communication diagrams.
- HUMINT situation overlays.
- HUMINT-related portions of the threat assessment.
- CI target lists.
b. The analytical techniques used in HUMINT analysis enable the analyst to visualize large amounts of data in graphic form. We emphasize, however, that these analytical techniques are only tools used to arrive at a logical and correct solution to a complex problem; the techniques themselves are not the solution.
c. There are three basic techniques (tools) used as aids in analyzing HUMINT-related problems. These techniques—time event charting, matrix manipulation, and link diagraming—used together, are critical to the process of transforming diverse and incomplete bits of seemingly unrelated data into an understandable overview of an exceedingly complex situation.
(1) Time event charting.
(a) The time event chart shown in Figure A-VI-1, is a chronological record of individual or group activities designed to store and display large amounts of information in as little space as possible. This tool is easy to prepare, understand, and use. Symbols used in time event charting are very simple. Analysts use triangles to show the beginning and end of the chart. They also use triangles within the chart to show shifts in method of operation or change in ideology. Rectangles or diamonds are used to indicate significant events or activities.
(b) Analysts can highlight particularly noteworthy or important events by drawing an "X" through the event symbol (rectangle or diamond). Each of these symbols contains a chronological number (event number), date (day, month, and year of event), and may contain a file reference number. The incident description is a very brief explanation of the incident, and may include team size, type of incident or activity, place and method of operation, and duration of incident. Time flow is indicated by arrows.
(c) Analysts also use a variety of symbols such as parallelograms and pentagons, and others, to show different types of events and activities. Using these symbols and brief descriptions, the MDCI analyst can analyze the group's activities, transitions, trends, and operational patterns. Time event charts are excellent briefing aids as well as flexible analytical tools.
(2) Matrix manipulation.
(a) Construction of a matrix is the easiest and simplest way to show relationships between similar or dissimilar associated items. The "items" can be anything relevant to the situation under investigation: persons, events, addressees, organizations, or telephone numbers. During this process, MDCI analysts use matrices to determine "who knows whom" or "who has been where or done what." This results in a clear and concise display which viewers can easily understand simply by looking at the matrix.
(b) In general terms, matrices resemble the mileage charts commonly found in a road atlas. Within the category of matrices, there are two types used in investigative analysis—association matrix and activities matrix.

1 Association matrix. The association matrix is used to show that a relationship between individuals exists. Within the realm of HUMINT analysis, the part of the problem deserving the most analytical effort is the group itself. Analysts examine the group's elements (members) and their relationships with other members, other groups and associated entities, and related events. Analysts can show the connections between key players in any event or activity in an association matrix shown in Figure A-VI-2. It shows associations within a group or similar activity, and is based on the assumption that people involved in a collective activity know one another.

a This type of matrix is constructed in the form of a right triangle having the same number of rows and columns. Analysts list personalities in exactly the same order along both the rows and columns to ensure that all possible associations are shown correctly. The purpose of the personality matrix is to show who knows whom. Analysts determine a known association by "direct contact" between individuals. They determine direct contact by a number of factors, including face-to-face meetings, confirmed telephonic conversation between known parties, and all members of a particular organizational cell.
NOTE: When a person of interest dies, a diamond is drawn next to his or her name on the matrix.
b MDCI analysts indicate a known association between individuals on the matrix by a dot or filled-in circle. They consider suspected or "weak" associations between persons of interest to be associations which are possible or even probable, but cannot be confirmed using the above criteria. Examples of suspected associations include—
A known party calling a known telephone number (the analyst knows to whom the telephone number is listed), but cannot determine with certainty who answered the call.
The analyst can identify one party to a face-to-face meeting, but may be able to only tentatively identify the other party
.
(c) Weak or suspected associations on the personality matrix are indicated by an open circle. The rationale for depicting suspected associations is to get as close as possible to an objective analytic solution while staying as close as possible to known or confirmed facts. If analysts can confirm a suspected association, they can make the appropriate adjustment on the personality matrix.
(d) A secondary reason for depicting suspected associations is that it may give the analyst a focus for tasking limited intelligence collection assets to confirm the suspected association. An important point to remember about using the personality matrix: it will show only that relationships exist; not the nature, degree, or frequency of those relationships.
2 Activities matrix. The activities matrix is used to determine connectivity between individuals and any organization, event, entity, address, activity, or anything other than persons. Unlike the association matrix, the activities matrix is constructed in the form of a square or a rectangle as shown in Figure A-VI-3. It does not necessarily have the same number of rows and columns. The analyst can tailor rows or columns to fit the needs of the problem at hand or add them later as the problem expands in scope. The analyst determines the number of rows and columns by the needs of the problem and by the amount of information available.
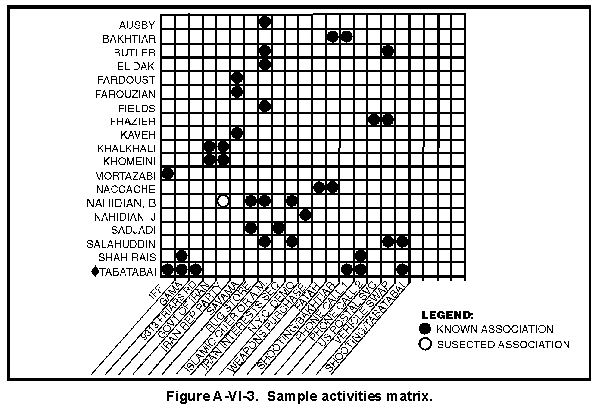
a Analysts normally construct this matrix with personalities arranged in a vertical listing on the left side of the matrix; and activities, organizations, events, addresses, or any other common denominator arranged along the bottom of the matrix.
b This matrix can store an incredible amount of information about a particular organization or group, and can build on information developed in the association matrix. Starting with fragmentary information, the activities matrix can reveal an organization's—
- Membership.
- Organizational structure.
- Cell structures and size.
- Communications network.
- Support structure.
- Linkages with other organizations and entities.
- Group activities and operations.
- Organizational and national or international ties.
c As with the association matrix, known association between persons and entities is indicated by a solid circle, and suspected associations by an open circle.
d Analysts use matrices to present briefings, present evidence, or store information in a concise and understandable manner within a database. Matrices augment, but cannot replace, standard reporting procedures or standard database files. Using matrices, the analyst can—
- Pinpoint the optimal targets for further intelligence collection.
- Identify key personalities within an organization.
- Increase the analyst's understanding of an organization and its structure.
NOTE: The graphics involved in constructing the two types of matrices differ slightly, but the principles are the same.
(3) Link diagraming. The third analytical technique is link diagraming shown in Figure A-VI-4. Analysts use this technique to depict the more complex linkages between a large number of entities, be they persons, events, organizations, or almost anything else. Analysts use link analysis in a variety of complex investigative efforts including criminal investigations, terrorism, analysis, and even medical research. Several regional law enforcement training centers are currently teaching this method as a technique in combatting organized crime. The particular method discussed here is an adaptation especially useful in CI investigative analysis in general and terrorism analysis in particular.
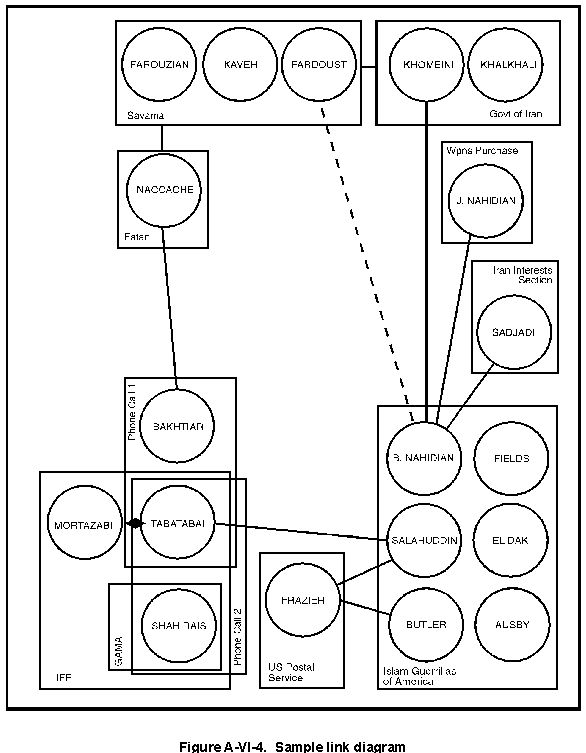
(a) The difference between matrices and link analysis is roughly the same as the difference between a mileage chart and a road map. The mileage chart shows the connections between cities using numbers to represent travel distances. The map uses symbols that represent cities, locations, and roads to show how two or more locations are linked to each other. Different symbols on the map have different meanings, and it is easy to display or discover the best route between two or more locations as well as identify obstacles such as unpaved roads or bodies of water.
(b) The same is true with link analysis. Different symbols are used to identify different items. Analysts can easily and clearly display obstacles, indirect routes or connections, and suspected connections. In many cases, the viewer can work with and follow the picture easier than the matrix. Link analysis can present information in a manner that ensures clarity.
(c) As with construction of association matrices, certain rules of graphics, symbology, and construction must be followed. Standardization is critical to ensure that everyone constructing, using, or reading a link diagram understands exactly what the diagram depicts. The standard rules follow:
- Show persons as open circles with the name written inside the circle.
- Show persons known by more than one name (alias, also known as [AKA]) as overlapping circles with names in each circle.
- Show deceased persons as above, with a diamond next to the circle representing that person.
- Show nonpersonal entities (organizations, governments, events, locations) by squares or rectangles.
- Show linkages or associations by lines: solid for confirmed and dotted for suspected.
- Show each person or nonpersonal entity only once in a link diagram.
(d) Certain conventions must be followed. For the sake of clarity, analysts arrange circles and squares so that whenever possible, lines of connectivity do not cross. Often, particularly when dealing with a large or especially complex problem, it is difficult to construct a link diagram so that no connecting lines cross. Intersecting lines, however, muddle the drawing and reduce clarity. If lines must cross, show the crossing as a crossing, not as an intersection, in exactly the same manner as on an electrical schematic or diagram.
(e) Link diagrams can show organizations, membership within the organization, action teams or cells, or participants in an event. Since each individual depicted on a link diagram is shown only once, and some individuals may belong to more than one organization or take part in more than one event, squares or rectangles representing nonpersonal entities may overlap.
(f) Construct the appropriate association matrices showing "who knows whom," "who participated in what," "who went where," and "who belongs to what group."
(g) Draw information from the database and intelligence reports, and relationships from the matrices. Group persons into organizations or cells based on information about joint association, activities, or membership. Draw lines representing connections between individuals, organizations, or activities to complete the diagram. You may have to rearrange the diagram to comply with procedural guidelines, such as crossed lines of connectivity. The finished product will clearly display linkages between individuals, organizations, and other groupings.
(h) When you finish the matrices and link diagram, make recommendations about the group's structure. Identify areas for further intelligence collection targeting. Task intelligence assets to confirm suspected linkages and identify key personalities for exploitation or neutralization. The combination of matrix manipulation and the link diagram present, in effect, a graphic depiction of an extremely complex threat situation in a clear and concise picture.
(i) Overlapping organizations.
1 There is more to overlapping organizations than is immediately obvious. At first glance, the overlap indicates only that an individual may belong to more than one organization or has taken part in multiple activities. Further study and analysis would reveal connections between organizations, connections between events, or connections between organizations and events.
2 When, as is often the case, an organization or incident shown in a link diagram contains the names of more than one individual, it is not necessary to draw a solid line between those individuals to indicate connectivity. We assume that individual members of the same group or participants in the same activity know each other, and the connection between them is therefore implied.
(j) A final set of rules for link diagrams concerns connectivity between individuals who are not members of an organization or participants in an activity, but who are somehow connected to the group or activity. Two possibilities exist: The individual knows a member or members of the organization but is not directly connected with the organization itself. The person is somehow connected with the organization or activity but cannot be directly linked with any particular member of that organization or activity. In the first case, draw the connectivity line between the circle representing the individual and the circle representing the person within the organization or activity.
(k) If you keep in mind the preceding outline of principles and rules, you can construct a link diagram effectively. Because this is a rather complex form of analytical graphic display to construct, it may prove difficult at first and require a little extra time and effort. The payoff, however, is the powerful impact of the results, which are well worth the extra effort.
Section VII
PERSONNEL SECURITY INVESTIGATIONS
TO
Appendix A
COUNTER-HUMAN INTELLIGENCE TECHNIQUES AND PROCEDURES
A-VII-1. Personnel Security Investigations.
CI agents conduct PSIs on individuals requiring access to classified information. DIS Manual 20-1-M contains personnel security investigative requirements, types and scope of investigations, and the criteria for each component of a PSI. It also contains the methods and procedures governing the conduct of PSIs. In CONUS, DIS conducts PSIs; and OCONUS, the military services conduct PSIs on behalf of DIS.
a. There are several types of PSIs. Each type provides the individual with a different level of access to classified information. The types of PSIs are national agency checks (NACs), single scope background investigations (SSBIs), and LAA.
(1) NAC. An NAC consists, as a minimum, of a check of the Defense Central Index of Investigations (DCII) and the FBI. The FBI check is a review of files for information of a security nature which is developed during applicant-type investigations. It also includes a technical fingerprint search (classification of SUBJECT's fingerprints and comparison with fingerprints on file). If the fingerprint card is not classifiable, a "name check only" is automatically conducted. Office of Personnel Management, INS, State Department, CIA, and other federal agencies also may be checked, depending on the case. An NAC is the minimum investigative requirement for a final SECRET clearance for military personnel. It may be used as a basis for an interim TOP SECRET clearance based on simultaneous submission of a request for a background investigation.
(2) SSBI. An SSBI consists of a records review NAC, interviews with sources of information, and a subject interview; the subject interview being the principal component. The SSBI covers the most recent 10 years of an individual's life or 18th birthday, whichever is shorter, provided the last two years are covered. No investigation is made for the period before the individual's 16th birthday. The SSBI includes local agency checks, interviews of developed character references, employment references with employment records checks, education records checks and interviews, interviews of neighbors at previous residences, credit checks, citizenship verification, plus selected follow-up interviews as required to resolve unfavorable or questionable information. An SSBI is the minimum investigative requirement for granting a final TOP SECRET security clearance or for participation in certain special programs.
(3) LAA. An LAA is the formal authority granted to non-US citizens to have access to specifically prescribed and limited US classified defense information and materials. In each case, an investigation equivalent to the SSBI in scope must be completed with favorable results. A polygraph may be used to compensate for those portions of the SSBI which cannot be accomplished due to geographic or procedural limitations. An LAA may remain in effect for a maximum of five years before reinvestigation.
b. DIS Manual 20-1-M contains a full explanation of PSI requirements and criteria.
A-VII-2. PSI Reference Interview.
Before conducting a PSI Reference (Source) Interview, the CI agent must carefully examine all available background information on the case without exceeding the agent's standing investigative authority, which allows checks of sources only when identity or reliability is questioned. The SUBJECT of the investigation may have submitted a DD Form 398 which is often the initial source of leads. It may indicate the relationship between the listed references and the subject. It may also assist in creating a mental picture of the SUBJECT—an invaluable aid in formulating a line of questioning for an interview.
a. Source interviews may be tasked by some form of lead sheet, which normally contains limited background information. Leads may also be developed through previous investigative activity. Unit files, local and Federal law enforcement agency files, telephone books, and city directories are all sources of information on both the SUBJECT and potential sources. It is desirable and necessary in critical cases, where the credibility of an interviewee is questionable, to learn something about the Source. A telephone call to arrange an appointment with a prospective Source is a courtesy that is often helpful to the investigator. The final preparatory step is to form a tentative plan for questioning the Source.
b. The approach to a PSI Reference (Source) Interview is simply an application of the social code of polite behavior, together with certain investigative requirements. The CI agent must—
(1) Determine that the right person has been contacted, using the full name of the interviewee or Source to prevent any possibility of error.
(2) Identify the SUBJECT of the investigation and find out if the Source is or was acquainted with the SUBJECT.
(3) Present credentials to the Source for inspection, even if the individual was previously contacted by telephone.
(4) Ensure, to the extent possible, that the interview will not be interrupted or overheard. Emphasize the US Army policy limiting dissemination of details of an investigation.
(5) Explain the purpose of the interview to the Source. The CI agent should emphasize the importance the Source's knowledge may have to the investigation. Some people are inclined to look with suspicion at investigators and are reluctant to give information. A patient explanation of the purpose of the interview, and the important part the Source's cooperation may play, may be sufficient to allay this general suspicion and forestall any reluctance to provide information.
(6) Inform the Source that the interview and the matters discussed are regarded by the US Army as official US Army business and should not be discussed with other persons, especially the SUBJECT of the investigation.
(7) Advise the Source of the Privacy Act of 1974. Ask the Source if there are any objections to the release of the interviewee's name as the source of the information. This advisement should be given at the termination of the interview to both US citizens and resident aliens, unless Source raised the question of disclosure earlier in the interview. OCONUS interviews of foreign nationals, who are not US resident aliens, do not require a Privacy Act advisement.
(8) Establish rapport with the Source before beginning the interview. Proper rapport creates a mutual understanding between the parties of the interview. Professional appearance, a pleasant voice, a courteous demeanor, and a confident manner are all important. The burden for maintaining rapport throughout an interview rests with the CI agent. An interview normally takes place in the Source's home or place of work, where the individual is under no official compulsion to furnish the information sought. Topics of mutual interest should be used to help establish rapport, but caution must be exercised to keep the interview from becoming a casual conversation.
c. Once a Source is willing to cooperate, begin the questioning to establish the period of association with the SUBJECT and the extent of personal knowledge of the SUBJECT.
(1) The period of association consists of—
(a) When the Source and the SUBJECT first met and under what circumstances.
(b) When they last met and under what circumstances.
(c) All periods of association.
(d) Types of association, such as friends, coworkers, or both.
(e) Frequency of contact, for both social and professional association.
(f) Breaks in contact for periods of 30 days or more.
(g) Whether there has been any form of communication between them since their last contact.
(2) This information also aids in developing systematic questions on the loyalty, integrity, discretion, and moral character of the SUBJECT. It is important that the CI agent lay a framework for the interview, through a thorough understanding of the association between the Source and the SUBJECT. In addition, the association area may disclose leads which may be exploited later.
d. The CI agent must exploit all aspects of the SUBJECT's background. The CI agent must be constantly alert for leads to other persons not listed by the SUBJECT as references. If the Source is or was an employee or coworker of the SUBJECT, attention should focus on the efficiency, initiative, and ability of the SUBJECT to get along with fellow workers and subordinates and on the SUBJECT's honesty, reliability, and general character. If the Source is or was a neighbor of the SUBJECT, the CI agent should discuss the SUBJECT's general reputation, family, leisure time activities, morals, and personal habits. Concentration on some points does not imply exclusion of others.
e. The CI agent must seek information which will assist in establishing the SUBJECTs loyalty, trustworthiness, and suitability. Figure A-VII-1 shows the general area of interest for an interview and a basis for discussion.
f. Avoid questions concerning religious beliefs, racial matters, politics, labor affiliations, or personal and domestic matters, unless absolutely essential to the investigation; such questions not relevant to the purpose of the interview constitute unnecessary and unwarranted invasion of the SUBJECT's privacy.
g. The CI agent, as a representative of MI, should be professional in manner and efficient in the execution of duty. The agent must be receptive and flexible.
(1) The agent should dress either in civilian clothes or uniform according to assigned duty and mission. The agent pinpoints specific information desired and avoids general questions. When the Source states, for example, that the SUBJECT is an indiscreet person, request that the Source cite specific examples to support this opinion. If the Source claims the SUBJECT is a drunkard, the individual's definition of the term should be clearly established and specific details obtained.
(2) Analyze each phase of the SUBJECT's background point-by-point.
(3) If the Source presents information in a haphazard manner, the CI agent should guide the discussion into a logical pattern.
A-VII-3. PSI SUBJECT Interview.
a. CI agents conduct SUBJECT Interviews when tasked by DIS in the lead sheet.
b. If the SUBJECT is suspected of violating the law, the CI agent must advise the individual of rights under the provisions of the Fifth Amendment to the US Constitution or Article 31, UCMJ, as appropriate. The CI agent must remember that the SUBJECT has the right to legal advice at any time before, during, or after the interview. Note that there are no noncustodial interviews involving a military member according to Article 31, UCMJ.
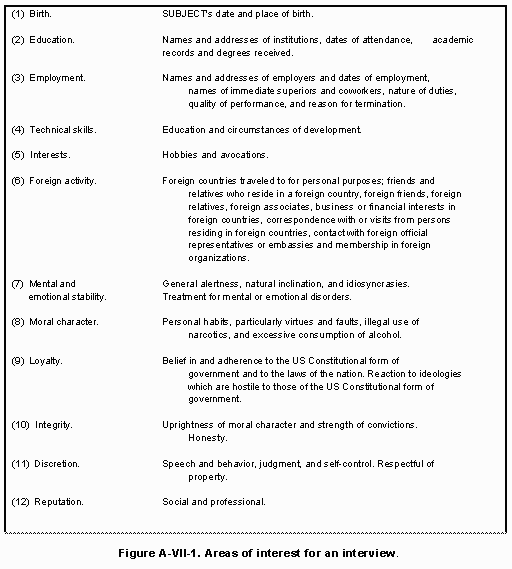
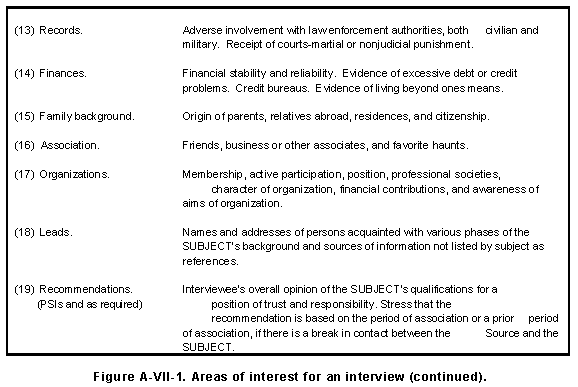
c. The CI agent should not raise questions concerning religious beliefs, racial matters, politics, labor affiliations, or personal and domestic matters unless directly related to the investigation. The CI agent should phrase and time such questions so as to clearly establish the fact that they are relevant to the investigation.
d. To prepare for a SUBJECT Interview, the CI agent—
(1) Contacts the SUBJECT and informs the individual of the reason for the interview. In most cases, the matters to be discussed will not come as a surprise to the SUBJECT. The CI agent tells the SUBJECT that the interview gives the individual an opportunity to explain, refute, or mitigate, questionable or misleading information, and to provide information not otherwise obtainable. If the SUBJECT is willing to be interviewed, the CI agent arranges the time, date, and place for the interview. If the SUBJECT refuses to be interviewed or to answer questions, an official record should be made of the refusal. Provide a brief advisement to the SUBJECT that failure to provide information may adversely affect the processing of the SUBJECT's security clearance.
(2) Gathers all lead information before the interview. Carefully reviews preplanned questions for each interview so that only information specifically authorized by the control office is released to the SUBJECT during the interview.
(3) Ensures that the SUBJECT understands that upon request, and if the individual is called to appear before a field board of inquiry or a civilian security hearing board, the SUBJECT will be provided a copy of any statement provided during the interview. However, the restrictions in AR 380-5 on the release of classified information apply.
(4) Ensures the SUBJECT's copy will not bear a protective marking but will contain a statement substantially as follows: "A copy of (describe) is furnished at your request. The official copies of this document will be protected to safeguard your confidence and will be used for official purposes only."
e. In accordance with the Privacy Act of 1974, whenever a CI agent interviews a SUBJECT, the agent must give the SUBJECT a four-point Privacy Act Advisement. In cases where an advisement of rights is required, the CI agent should provide the SUBJECT with the Privacy Act Advisement statement before the SUBJECT is advised of individual rights under Article 31, UCMJ, or the Fifth Amendment to the US Constitution.
(1) The CI agent should provide the SUBJECT with two copies of the advisement statement. One copy is for the individual's retention, if desired. The CI agent will request the SUBJECT sign the other copy and return it. Privacy Act of 1974 statements are retained but not attached as part of the report.
(2) DIS Manual 20-1-M covers Privacy Act Advisement procedures during the conduct of a PSI under the control of DIS.
(3) The CI agent will verbally inform the SUBJECT that the Privacy Act of 1974 requires that each individual asked to provide personal information be advised of the following four points:
(a) Authority by which the information is being collected.
(b) Principal purpose for which the information will be used.
(c) Routine uses of the information.
(d) Voluntary nature of disclosing information.
(4) Before highlighting the four points, the CI agent should allow sufficient time for the SUBJECT to read the advisement statement.
(5) After highlighting the four points, ask the individual to sign one copy before beginning the interview.
f. During conduct of SUBJECT Interview, the SUBJECT perceives the CI agent as being a representative of the US Army. As such, the SUBJECT will regard the CI agent's every statement, question, or contact as part of the official proceeding, whether so intended or not. During the interview, the CI agent will—
- Make no off-the-record or unofficial remarks in the interview, nor any promises or commitments to the SUBJECT which are beyond the CI agent's legal authority to fulfill.
- Avoid statements or representations which may be construed as opinion or advice to the SUBJECT about past, present, or future actions. CI agents should not argue with the SUBJECT or express personal viewpoints on any matter.
- Obtain permission from the SUBJECT if a tape or other recorder is to be used during the interview. DIS Manual 20-1-M does not require the use of a tape or other recording device. Take the following actions in the sequence listed. If not recording, omit portions that pertain to the recorder.
(a) Dictate identifying data into a tape recorder before the SUBJECT's arrival. Turn off the machine.
(b) Visually identify the SUBJECT; identify yourself and present credentials; and positively identify the SUBJECT through the use of a pictured ID card, recording all pertinent information from the ID card.
(c) Explain the general purpose and confidential nature of the interview.
(d) Obtain permission to record the interview. Explain that it will facilitate the preparation of a written transcript of the interview, which the SUBJECT will have an opportunity to review, correct, and sign under oath.
(e) Turn on the tape recorder. If the SUBJECT objects to the tape recorder, do not use it. Proceed, but take notes as accurately as possible, while maintaining close attention to the SUBJECT's verbal answers and physical reactions. A tape recording is an administrative convenience, but not having one will not unduly hamper taking the sworn statement and preparing the report.
(f) Administer a full explanation of rights (if required). Request the SUBJECT read and sign DA Form 3881 to acknowledge receipt of the explanation of rights; and to record the individual's decision to exercise or waive the right to remain silent and to consult counsel. If the individual exercises his or her right to silence or to consult counsel, the interview should terminate at this point.
(g) Advise the SUBJECT of the provisions of the Privacy Act of 1974. The CI agent will request the SUBJECT complete the Privacy Act of 1974 Advisement Statement.
(h) Explain to the SUBJECT the DA policy allowing SUBJECTs of investigations every reasonable opportunity to explain, refute, or mitigate information which is developed during the course of an investigation. Furthermore, explain that this is the individual's opportunity to provide whatever information the SUBJECT feels appropriate.
(i) Though not required by DIS Manual 20-1-M, the CI agent may administer the oath of truthfulness to the SUBJECT, following the explanation and acknowledgment of legal rights, but before asking any questions. An appropriate oath is: "Do you affirm that the statements you are about to make are the truth, the whole truth, and nothing but the truth?" Additional remarks such as "So help you God" are unnecessary and may be offensive. If the SUBJECT refuses to take an oath, ask why, then proceed.
(j) Ask the SUBJECT to state his or her name, rank, SSN, DPOB, unit of assignment, duty position, and residence address for the record.
(k) Conduct the interview using the questions from DIS Manual 20-1-M that cover the appropriate topics and prepared questions designed to elicit narrative answers. These prepared questions are only a guide and are not intended to be the only questions asked. The CI agent must fully develop all information provided by the SUBJECT. Record and report all answers accurately.
(l) Make arrangements for the SUBJECT to review and sign a typewritten sworn statement, before ending the interview.
(m) Thank the SUBJECT for cooperating and terminate the interview. - ********************************************************************************
I would remind any and everyone: You do NOT know that :,
May your walls fall and may I live to tell....
May all the world forget you ever stood....
And may all the world regret you did no good.
Nixon White House Plot to Murder a Newspaper Columnist ... clips
of Liddy discussing his involvement in plotting to kill
newspaper columnist Jack An...
www.youtube.com/watch?v=aNOQ6SDOaYI
----------------------------------------------------------------
Title: A Report on CIA Infiltration and Manipulation of the Mass
Media ..... Former CIA director William Colby claimed in 1973 to
have scaled back c...
www.geocities.com/cpa_blacktown/20000318mediaoverb.htm
------------------------------------------------------------------
It turns out that the infiltration program was itself
infiltrated from the ... Instead, the media ring with praise for
Colby, the man who opened up ...
mediafilter.org/caq/CAQ57briefs.html
------------------------------------------------------------------
Media Mind Control
"Let's not pick on some reporters," CIA Director William Colby
stated. ... infiltration of the corporate media, a process that
often included direct ....
www.takeoverworld.info/media.html
------------------------------------------------------------------
been discovered eight days prior.
www.freerepublic.com/china/24.htm
------------------------------------------------------------------
Sherman Skolnick's Report
... and guard while President John F. Kennedy's motorcade slowed
down to a crawl ... friends of Colby know Colby was murdered and
made to look like a ...
www.skolnicksreport.com/ootar15.html
------------------------------------------------------------------
The murder of JFK Jr. and others...
For four years now the world has slept while William Colby
decided to abandon his hot dinner and take a final canoe ride,
while Vince Foster chose to ...
yitchakrabin.com/Barry%20Chamish/html/jfk_jr_murder.html
------------------------------------------------------------------
William Colby - The Education Forum
On 28th April 1996 William Colby went on a canoe trip at Rock
Point, .... "Dead CIA Chief Was Set To Finally Blow Lid on JFK
Assassination". ...
educationforum.ipbhost.com/index.php?showtopic=7144
------------------------------------------------------------------
Who Killed JFK?
Dorothy Kilgallen, a prominent columnist and TV personality, was
ruled a suicide by drug overdose in November 1965. She had just
completed a lengthy...
www.thirdworldtraveler.com/CIA/Who_Killed_JFK.html
------------------------------------------------------------------
YouTube - George W. Guilty of Murder....
A French journalist has just released a movie called :" George W". ...
lawyer lays out a compelling case in THE PROSECUTION OF GEORGE W.
BUSH FOR MU...
www.youtube.com/watch?v=jRlJk1qhWVw
French journalist has just released a movie called :" George W".
In it is stated that George W and Dick Cheney each acquired a
ranch in Paraguay. Paraguay has no extradition laws. Nazis knew
it and fled there after WW2 was lost. "THEY" know better.
indysuperdave (2 weeks ago)
Reply Its Sad What He Said Is True What's Even Worse He Will
Never Be Prosecuted....?
http://www.politicalstrategy.org/archives/000354.php
Rove was able to suppress the book. Hatfield is said to have
died under mysterious circumstances, not unlike Margie
Schrödinger, a woman who dated Bush in high school and charged
before her death that Bush had drug and raped her
While Hatfield's felony was essentially an unrelated work
dispute, Rove used that crime record to pressure St. Martin's
into the unusual step of withdrawing and BURNING the book.
Mainstream media ran once than quickly buried the book's story.
"Fortunate Son" was later re-issued by SoftSkull Press. You can
find it on Amazon.
everything that has gone wrong with the media. This remarkable
story includes ABC's takeover by a conservative parent
corporation, the demise of the Fairness Doctrine, the rightward
shift of the evening news, the rise of conservative talk radio,
and the cozy relationship between a state and a press that are
supposed to be separate.
In 1985, ABC was taken over by Capital Cities, a conservative,
Roman Catholic media organization with extensive ties to the CIA.
One of Capital City's early founders was William Casey, who
would later become Ronald Reagan's Director of the CIA. At the
time of Casey's nomination, the press expressed surprise that
Reagan would hire a businessman whose last-known intelligence
experience was limited to OSS operations in World War II. The
fact is, however, that Casey had never left intelligence.
Throughout the Cold War he kept a foot in both worlds, in
private business as well as the CIA. A history of Casey's
business dealings reveals that he was an aggressive player who
saw nothing wrong with bending the law to further his own
conservative agenda. When he became implicated as a central
figure in the Iran-Contra scandal, many Washington insiders
considered it a predictable continuation of a very shady career.
Another Capital Cities founder, Lowell Thomas, was a close
friend and business contact with Allen Dulles, Eisenhower's CIA
Director, and John Dulles, the Secretary of State. Thomas always
denied being a spy, but he was frequently seen at events
involving intelligence operations. Another founder was Thomas
Dewey, whom the CIA had given millions to create other front
companies for covert operations.
Capital Cities prospered from the start; its specialty was to
buy media organizations that were in trouble. Upon acquisition,
it would improve management and eliminate waste until the
company started turning a profit. This no-nonsense, no-frills
approach, as well as its refusal to become side-tracked with
other ventures, made it one of the most successful media
conglomerates of the 60s and 70s. Of course, the journalistic
slant of its companies was decidedly conservative and
anticommunist. To anyone who believes that the government should
not control the press, the possibility that the CIA created a
media company to dispense conservative and Cold War propaganda
should be alarming. Rush Limbaugh himself calls freedom of the
press "the sweetest -- and most American -- words you will ever
find." (2) Apparently, he is unaware of the history of his own
employers.
The Fairness Doctrine was repealed in 1987 by the FCC. Reagan
had staffed the FCC with prominent media businessmen who were
intent on slashing government regulations- the equivalent of
letting the fox guard the chicken coop. Among the many other
regulations slashed during the Reagan years were anti-trust laws
that prevented the media from becoming a monopoly. Much of this
was done under heavy pressure by corporate lobbyists.
------------------------------------------------------------------
------------------------------------------------------------------
http://ciaschool.tripod.com/
If it can be done to John F. Kennedy in 1963, it can be done to
another president in the future. And we can't afford to have
coup d'états in America, no matter how cleverly orchestrated and
sinisterly contrived they may be. That cannot be permitted to
happen. And the way you prevent that from happening is to
expose those elements of government and society in this country
that were responsible for the killing of John F. Kennedy."
--Dr. Cyril Wecht, interviewed in the documentary,
The Men Who Killed Kennedy: Part 1: The Coup D'état
"Mr. Clinton better watch out if he comes down here [to Fort
Bragg]. He better have a bodyguard." --Jesse Helms, Republican
Senator from North Carolina, speaking on the 31st anniversary of
the JFK assassination, November 22, 1994. (Helm's comment
reflected the widespread hostility of the military establishment,
and its right-wing allies in Congress, to President Clinton's
efforts to decrease military spending in the post Cold War era,
and allow gays to serve in the military.)
"There are other ways to kill a leader these days -- you can
assassinate his character." --former presidential candidate Gary
Hart, quoted by David Talbot, "The Mother of All Cover-Ups,"
Salon, 15 September 2004
"There is a right-wing [apparatus] and I know what it is, I've
been there, I was part of it and, yes, they were trying to bring
down Bill Clinton by damaging him personally ... by any means
necessary." --conservative journalist David Brock, appearing on
CNN's Crossfire, 10 March 1998
"It was a small intricately knit right-wing conspiracy -- and
I'd like that clarified." --Ann Coulter, far-right TV pundit,
admitting her knowledge of an anti-Clinton conspiracy, quoted in
The Hartford Courant, 25 June 1999
------------------------------------------------------------------
http://multi-medium.net/
http://ciaschool.tripod.com/
Linda Tripp, Monica Lewinsky's "friend," stated on her resume
that she had been an "operations assistant" to Delta Force at
Fort Bragg and an "administrative assistant" at U.S. Army
Intelligence headquarters at Fort Meade. Linda Tripp described
her Army intelligence work as being an "assistant to the
director, handling correspondence, tracking of classified case
files ... assisted in the coordination of a far reaching
political, international mission." In her testimony before the
Senate Whitewater Committee in 1995, Tripp said: "I've worked
on the covert side of the Department of Defense..." Beyond that
she wouldn't elaborate, saying "the nature of this position is
classified." Tripp also speaks German fluently, suggesting
intelligence training.
Moreover, the CIA and the Pentagon have a history of placing
intelligence operatives in low-level staff positions at the
White House.* Tripp was originally hired by the Bush
administration and, under Clinton, was one of the few holdovers,
serving as an assistant to the White House Counsel, the office
of Vince Foster. Given what is now known about Tripp's exploits,
it is likely that she was a mole in the Counsel office, passing
information to the Pentagon and/or the CIA.
With Vince Foster's "suicide" in 1993, right-wing pundits --
notably Christopher Ruddy and his employer, CIA-connected
billionaire Richard Mellon Scaife -- began to circulate stories
that Foster's death was not a suicide, but rather a murder and
that President Bill Clinton and his wife, Hillary were behind it.
However, others have intimated that, instead of the Clintons, it
is suspected intelligence operative Linda Tripp who should be
scrutinized, having been the last person in the White House to
see Vince Foster alive. Indeed, it was Linda Tripp who served
Vince Foster his last meal, a cheeseburger and some M&M's, which
she brought to him on a cafeteria tray.
The fact that Linda Tripp's resume included a stint as an
operations assistant to Delta Force has raised eyebrows.
According to NBC investigative reporter, Robert Windrem, Delta
Force personnel have, over the years, been recruited by the CIA's
Special Activities Staff (SAS) for use in assassinations.
------------------------------------------------------------------
http://mypage.uniserve.ca/~synergy/pg3-17.htm
Media Manipulation Techniques
Firstly, the elite's foreign policy actions become more
transparent when one recognizes that practically all foreign
policy is designed to assist the elite in modern day colonialist
exploitation, which can be categorized into five basic tasks.
1. Protecting their existing foreign investments (e.g., Kuwait,
Panama, etc.)
2. Setting up new exploitation opportunities (e.g., Mexico,
former Soviet Union countries, etc.)
3. Giving support to another colonialist ally (e.g., England
with the Falklands, France with Vietnam, etc.)
4. Trying to prevent the total loss of a country's exploitation
potential by preventing the country from adopting either a
socialist or communist system of government (e.g., Guatemala,
Chile, El Salvador, etc.) 5. Attempting to destabilize and
overthrow anti-American or existing left-wing governments to
install puppets who will reestablish exploitation opportunities
(e.g., Iraq, Nicaragua, Cuba, Angola, etc.)
The catering for many of the functions is normally handed over
to the CIA, the operational arm of these various think tanks,
which then has the means at its disposal to covertly organize
and fund whatever paramilitary groups or individual operatives
(like Oliver North), that may be required to carry off the
function. The inherent covert nature of the CIA makes it a
formidable tool in the hands of the elite who wish to carry out
strategies that would not stand up well to public or legal
scrutiny. Some of the events especially the marriages of
convenience previously mentioned can turn out to be rather
socially unpleasant events, because proceeding with the
relationship usually involves snubbing the country's current
leaders. And that invariably leads to bad blood between the
rival forces.
Restricting News Coverage to the Elite's Version
------------------------------------------------------------------
I would remind any and everyone: You do NOT know,
cannot know, what really happened, in a murder case like
this. So do not be so damned opinionated about it.
You do not know if there is conspiracy, or not.
When someone is arrested, you have a false sense of
"closure". You do not know if a government arranged
to charge some random rapist/murderer with a second
rape/murder. They know that no one will question it.
If you say that there is "no reason for suspicion", or
"no evidence", I say that *any* time that a death occurs
in a highly political situation, there is some reason
for suspicion, for a raised eyebrow, for an extra-diligent
investigation.
To be deeply suspicious of some the characters who are
running around on the national stage, is not being merely
small-minded or politically opportunist......
------------------------------------------------------------------------------
Collection of personal and biometric data now a new "INT"
Traditionally, intelligence services have employed a number of intelligence collection methods to gather information. Human intelligence or "HUMINT" collects information from human intelligence assets; signals intelligence or "SIGINT" collects electronic signals; imagery intelligence or "IMINT" is dedicated to the collection of images from satellite and other reconnaissance platforms, and the list goes on.
However, there is a new "INT" on the block: "Identity Intelligence" or "I2." I2collects personally-identifiable data on individuals from biometrics such as fingerprints, facial recognition, gait analysis, human identification-at-a-distance, DNA, retina and iris scans, hand geometry and other personal data collection systems; financial data from automatic teller machine and credit and debit card transactions; and global positioning system data captured from the use of cell phones and Blackberry devices. When coupled with Geospatial intelligence (GEOINT), I2 can be displayed on large scale and work station electronic maps in intelligence fusion centers that have been popularized by movies such as "Body of Lies" and "Quantum Solace."
I was the first to report that many of the massive thefts of personal data were being carried out by a super-secret unit within the U.S. intelligence community that wanted to collect personal data after the Total Information Awareness (TIA) system of the Defense Advance Research Projects Agency's Information Awareness Office and its then-chief, Iran-contra figure Admiral John Poindexter, were hauled on the carpet by Congress over the privacy-invasive system. Congress de-funded TIA but it re-emerged in a more clandestine environment within the National Security Agency (NSA) and Homeland Security Department, funded covertly with money laundered through the Department of Energy and its research laboratories.
Some I2systems are apparently being integrated in geo-spatial systems in order to find individuals in even remote locations. Operation Enduring Freedom - Trans Sahara (OEF-TS) and its military component, the Trans-Sahara Counter Terrorism Initiative (TSCTI), which targets nomadic peoples in the Sahara Desert who are thought to be "terrorists," employs I2 and GEOINT under classified programs with such cover names as Creek Sand and Aztec Archer.
I2 is such a hot new area of intelligence, and the CIA is sponsoring an Identity Intelligence Conference for only properly cleared personnel.
It is also apparent that I2 is being actively supported by a number of high-tech firms, including Microsoft, Oracle,Yahoo, SUN and Google.... plus many more worldwide....
---------------------------------------------------------------------------------------------------------------------------------------
Bust-up reveals major espionage operation by Jewish state .
The Federal Bureau of Investigation (FBI) has dismissed reports by Intelligence Online, a French website that specializes in security matters, on March 4 and expanded on by Le Monde the following day that US authorities had arrested or deported some 120 Israelis since February 2001 and that the investigation was still going on. The FBI insists that no Israeli has been charged with espionage, but that an undisclosed number of Israeli students have been expelled for immigration violations. Justice Department spokeswoman Susan Dryden dismissed the espionage allegations as “an urban myth that’s been circulating for months.”
There has been a blizzard of bizarre conspiracy theories since the Sept. 11 attacks, but the details that are slowly emerging despite what seems to be a news blackout on the mysterious Israelis sets this affair apart. If the reports from Paris are correct, it would be the largest known Israeli espionage operation ever mounted in the US, the Jewish state’s closest ally and one on which it has depended for its survival.
Israel has been spying on the US and running clandestine operations since the Jewish state was established, from spiriting out an estimated 90 kilograms of weapons-grade uranium for its secret nuclear arms program in the 1960s to widescale industrial espionage. Much of this is conducted by the highly secret Scientific Liaison Bureau, known by its Hebrew acronym Lakam and run by the Defense Ministry, and its equally little-known successor, Malmab (the Security Authority for the Ministry of Defense).
Indeed, the General Accounting Office, the investigative arm of Congress, reported in April 1996 that Israel “conducts the most aggressive espionage operation against the United States of any US ally.” It is not the only US government agency to condemn the Israelis on this. But no action, publicly at least, seems to have been taken to prevent this or warning Israel to stop such illegal activities or face the consequences.
The affair of the alleged Israeli spy ring, the official dismissals of anything untoward having happened and the almost total lack of investigative news coverage by the US media follows a pattern that has been discerned in recent years where illegal activities by Israeli intelligence organizations have allegedly been committed. This stems in large part from the powerful pro-Israel lobby in the US, the willingness of Congress to look the other way and the concern of successive administrations to avoid disturbing the strategic relationship with the Jewish state.
While the operation described by Intelligence Online and Le Monde is unlikely to have caused anywhere near the damage to US security inflicted by US Navy analyst Jonathan Pollard, an American Jew and Zionist who was sentenced to life imprisonment in 1987 for providing Israeli intelligence with a mountain of top secret material in 1984-85, it would still be political dynamite which could backfire on Israel as it finds itself increasingly isolated internationally over the intifada.
The reports of the operation were both based on a 61-page report compiled by a US inter-agency task force, dated June-July 2001, summarizing the information gleaned from questioning of the arrested Israelis. The Drug Enforcement Administration (DEA) headed the investigation because its internal security unit had first come across the “unusual behavior of young Israeli nationals who had gained access to DEA circles.” The DEA has access to other departments and is a key agency in tracking laundered money used by drug cartels and terrorist groups such as Al-Qaeda.
These people, it said, had posed as students selling art works and handicrafts, but in fact many of them had “served in military intelligence, electronic interception and/or explosive ordnance units” in the Israeli Army.
This appeared to tie in with a short report carried by The Washington Post one of the few on this subject carried by the US media in late November that 60 Israelis had been detained in the nationwide roundup of terrorist suspects after Sept. 11. It said that Immigration and Naturalization Service officials testified in court hearings related to the arrests that this group was “of special interest to the government.”
No subsequent reports on this group, most of whom faced immigration violations such as expired visas, appeared in the US media until Dec. 11, when the Fox News television channel began a four-part report on the mysterious Israelis and said that around 140 Israelis had been detained across the US in an enormous investigation into a suspected espionage ring.
Fox quoted US investigators as saying that “some of the detainees … failed polygraph questions when asked about alleged surveillance activities against and in the United States. There is no indication that the Israelis were involved in the 9-11 attacks, but investigators suspect that they may have gathered intelligence about the attacks in advance, and did not share it” with US authorities. Fox reporter Carl Cameron quoted a highly placed investigator as saying that all evidence in the case had been classified.
Guillaume Dasquie, editor of Intelligence Online, said the inter-agency report listed the names of many of the Israelis, their passport numbers and in some cases even their intelligence service serial numbers. He said that US agents had kept the Israeli suspects under surveillance in Arkansas, California, Florida and Texas, where some groups resided at the same times as most of the Al-Qaeda operatives who hijacked airliners on Sept. 11 to carry out their suicide attacks.
Fox said in its highly detailed report that US communications facilities had been penetrated by Israeli intelligence through two Israeli-owned telecommunications companies, Comverse Infosys and Amdocs, which between them handle virtually all the billings records in the US. Some of the arrested “students,” it said, had worked for Amdocs and “other companies in Israel that specialize in wiretapping.”
The reference to Amdocs is particularly interesting, because in June 2000, federal authorities conducted a highly classified investigation that focused on Amdocs Corporation of Missouri into whether Israeli agents had used the software company to intercept telephone conversations between the White House, the State Department and other government departments. There had been suspicions about Amdocs as far back as 1996. However, officials said no evidence to substantiate the allegations had been found and reports of a major espionage problem were quickly smothered by the government.
Officials admitted that the entire investigation had become “radioactive” and “too hot to handle,” but declined to give any details. However, FBI officials at the time confirmed to some reporters that the Israelis were running a major eavesdropping operation that reached into the highest echelons of government, using chip implants in Israeli-designed equipment that allowed outsiders to listen in. The officials identified an Israeli couple among the clandestine operatives, an Amdocs subcontractor working on a telephone-billing system being developed at that time by the Central Intelligence Agency who was married to an Israeli woman working at the Israeli embassy in Washington and was possibly a Mossad agent.
The Washington-based Insight magazine, which broke that story with an extensive report by editors J. Michael Waller and Paul M. Rodriguez in June 2000 following what was described as a year-long investigation, said that in a search of the husband’s office the FBI found “a list of the FBI’s most sensitive telephone numbers, including the Bureau’s ‘black’ lines that FBI counter-intelligence used to keep track of the suspected Israeli spy operation.”
Then, as with the latest investigation, the US media largely ignored the report. The Israeli press didn’t but took the line that the material had been leaked to the media by US officials to embarrass Ehud Barak, then Israel’s prime minister, at a time when he was defying then-President Bill Clinton, who wanted Israel to halt the sale of Israeli-designed AWACS aircraft to China. And again, as far as US authorities were concerned, the whole issue was quietly dropped.
There was an earlier episode in January 1997 when the US National Security Agency (NSA), which conducts global surveillance of electronic communications, intercepted a discussion between the Mossad station chief in Washington and a superior in Tel Aviv. The conversation referred to someone codenamed “Mega” which suggested to US authorities that a senior US official could be providing high-level intelligence to Israel.
After The Washington Post reported on May 7 that the FBI was investigating, the Israelis, highly indignant that the Americans had the temerity to eavesdrop on their diplomatic communications, informed Washington through intelligence channels that “Mega” was the nickname that the Mossad used for the CIA’s Israel desk officer who liaises with his Israeli counterparts.
US investigators were highly skeptical of the Israeli explanation, and indeed Yossi Melman of Haaretz, an expert on Israeli intelligence, noted at the time that “Mega” need not refer to a person but possibly to an organization or a method of gathering information. In any event, that episode too simply withered away inconclusively as far as the media and the American public were concerned.
Both sides had an interest in sweeping the affair under the carpet because it threatened to open a Pandora’s Box that both preferred remain tightly screwed down, particularly with relations between President Clinton and Benjamin Netanyahu deteriorating badly over the Israeli leader’s efforts to sabotage the Middle East peace process in which Clinton, his eye on his place in history, was personally investing a great deal of time and energy. There was a potential for damaging political consequences in their strategic relationship that neither side wanted.
But the FBI remained concerned, if only because of loose ends left dangling from the Pollard affair, which for a time badly damaged US relations with Israel and has left deep resentment at Israel within the US intelligence and defense community. The biggest unsolved mystery from the Pollard affair was who told the spy’s Israeli handlers what documents he should steal. Pollard who pleaded guilty and thus never appeared in open court where Israeli intelligence’s activities could be exposed to the light of day told interrogators that he was given extremely specific instructions from his handlers during his twice-weekly meetings at the Washington apartment of an Israeli Embassy official near the Israeli mission.
Whoever it was, according to US officials, regularly specified by code names and numbers the files Pollard was required to steal, suggesting that he or she was a highly placed individual. If that is so, an Israeli mole in the upper echelons of the US government, presumably still active, could prove to be infinitely more serious than Pollard’s treason ever was.
The Israelis always insisted that the Pollard affair was a rogue operation run by the maverick Rafael “Rafi” Eitan, a longtime Israeli intelligence operative and protégé of Ariel Sharon. At the time, Eitan, who had headed the Mossad operation that captured Adolf Eichmann in Buenos Aires in 1960 and was involved in the uranium-smuggling operation from the US a few years later, ran Lakam, which operated separately from Mossad and other Israeli intelligence agencies.
During the 17 months Pollard was active, he stole more than 1,000 classified documents, some of them hundreds of pages long 360 cubic feet of them. More than 800 were classified as top secret. He and four other Israelis, including General (then Colonel) Aviem Sella, an Israeli Air Force officer who had led the long-range air strike that destroyed Saddam Hussein’s nuclear reactor in June 1981 and had recruited Pollard, were made the scapegoats (although both were rewarded for their work with Pollard) while the Israeli government swore blindly that it had not authorized the operation.
Officially, Lakam was disbanded almost immediately after Pollard’s arrest in Washington, but in fact was later resurrected as Malmab, specializing in ensuring the security of Israel’s military-industrial complex but also targeting potential competitors and engaging in industrial espionage to obtain technological secrets that even the Americans don’t pass on to their Israeli allies along with the estimated $80 billion in military aid the US has given Israel over the last two or three decades.
Malmab’s expanded mandate has antagonized the Mossad and other Israeli intelligence organizations. Indeed, Yediot Ahronot recently quoted one Mossad official as warning that Malmab, if left unchecked, “is likely to blow up in our faces in the same magnitude as the Jonathan Pollard case.”
Israeli defense officials insist that Malmab does not operate illegally, as Lakam did. That may or may not be true, but in November 1998, 10 months after Malmab’s existence was revealed, the US Defense Security Service disclosed in a report that 37 states were engaged in seeking to steal America’s military technology secrets. Although the report did not publicly name the countries, officials named Israel as one of the main perpetrators and the only major recipient of US aid to do so. “We used to call (France, Israel and Japan) our allies. Now we call them our non-traditional adversaries,” one intelligence consultant commented.
According to Duncan Clarke of the American University’s School of International Service in Washington, who wrote a damning paper on Israel’s industrial espionage activities in the US: “The United States and Israel agreed in 1951 not to spy on one another. There is little evidence that the United States has conducted economic espionage against Israel, but the agreement has been flouted repeatedly and flagrantly by Israel.
“Israeli economic espionage has infuriated the US intelligence community, especially the FBI and the Customs Service, and has left a legacy of distrust in that community. The greater concern, however, is not Israel’s behavior. Rather it is with those senior US officials and legislators who abide it.
“This aspect of the ‘special relationship’ with Israel annoys, even embitters, much of the permanent national security bureaucracy,” Clarke wrote. “It is also a latent domestic political issue with divisive overtones. Whatever immediate advantages Israel’s illicit practices may bring, they could eventually weaken the long-run relationship that is the ultimate guarantee of Israel’s security.”


